Security News
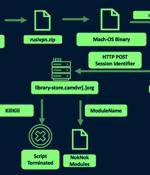
The Iranian nation-state actor known as TA453 has been linked to a new set of spear-phishing attacks that infect both Windows and macOS operating systems with malware. "TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho," Proofpoint said in a new report.
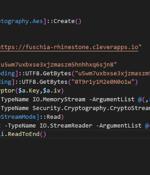
Charming Kitten, the nation-state actor affiliated with Iran's Islamic Revolutionary Guard Corps, has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured PowerShell backdoor called POWERSTAR. "There have been improved operational security measures placed in the malware to make it more difficult to analyze and collect intelligence," Volexity researchers Ankur Saini and Charlie Gardner said in a report published this week. Recent intrusions orchestrated by Charming Kitten have made use of other implants such as PowerLess and BellaCiao, suggesting that the group is utilizing an array of espionage tools at its disposal to realize its strategic objectives.

An unnamed government entity associated with the United Arab Emirates was targeted by a likely Iranian threat actor to breach the victim's Microsoft Exchange Server with a "Simple yet effective" backdoor dubbed PowerExchange. The custom implant achieves this by making use of the Exchange Web Services API to connect to the victim's Exchange Server and uses a mailbox on the server to send and receive encoded commands from its operator.

The Iranian threat actor known as Agrius is leveraging a new ransomware strain called Moneybird in its attacks targeting Israeli organizations. Agrius, also known as Pink Sandstorm, has a track record of staging destructive data-wiping attacks aimed at Israel under the guise of ransomware infections.

A suspected Iranian state-supported threat actor known as 'Agrius' is now deploying a new ransomware strain named 'Moneybird' against Israeli organizations. Check Point's researchers who discovered the new ransomware strain believe that Agrius developed it to help expand their operations, while the use of 'Moneybird' is yet another one of the threat group's attempts to cover their tracks.

At least eight websites associated with shipping, logistics, and financial services companies in Israel were targeted as part of a watering hole attack. Tel Aviv-based cybersecurity company ClearSky attributed the attacks with low confidence to an Iranian threat actor tracked as Tortoiseshell, which is also called Crimson Sandstorm, Imperial Kitten, and TA456.

Microsoft says Iranian state-backed hackers have joined the ongoing assault targeting vulnerable PaperCut MF/NG print management servers. "The PaperCut exploitation activity by Mint Sandstorm appears opportunistic, affecting organizations across sectors and geographies," the Microsoft Threat Intelligence team said.

A new Android surveillanceware possibly used by the Iranian government has been used to spy on over 300 individuals belonging to minority groups. "The spyware may also have been used in efforts to counter and monitor illegal trafficking activity related to arms, drugs, and alcohol," Lookout said, based on exfiltrated data that contained photos of drugs, firearms, and official documents issued by FARAJA. BouldSpy, like other Android malware families, abuses its access to Android's accessibility services and other intrusive permissions to harvest sensitive data such as web browser history, photos, contact lists, SMS logs, keystrokes, screenshots, clipboard content, microphone audio, and video call recordings.
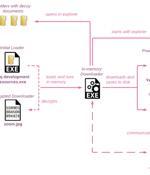
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that's designed to deploy an updated version of a backdoor called PowerLess. The attack chain documented by Check Point begins with an ISO disk image file that makes use of Iraq-themed lures to drop a custom in-memory downloader that ultimately launches the PowerLess implant.

An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022. Targeted entities consist of seaports, energy companies, transit systems, and a major U.S. utility and gas company.