Security News

An Iranian-linked threat actor known as Rocket Kitten has been observed actively exploiting a recently patched VMware vulnerability to gain initial access and deploy the Core Impact penetration testing tool on vulnerable systems. Tracked as CVE-2022-22954, the critical issue concerns a case of remote code execution vulnerability affecting VMware Workspace ONE Access and Identity Manager.
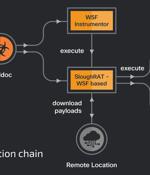
The Iranian state-sponsored threat actor known as MuddyWater has been attributed to a new swarm of attacks targeting Turkey and the Arabian Peninsula with the goal of deploying remote access trojans on compromised systems. "The MuddyWater supergroup is highly motivated and can use unauthorized access to conduct espionage, intellectual property theft, and deploy ransomware and destructive malware in an enterprise," Cisco Talos researchers Asheer Malhotra, Vitor Ventura, and Arnaud Zobec said in a report published today.

An Iranian geopolitical nexus threat actor has been uncovered deploying two new targeted malware that come with "Simple" backdoor functionalities as part of an intrusion against an unnamed Middle East government entity in November 2021. The attacks are said to have been orchestrated via spear-phishing messages to gain initial access, followed by taking advantage of publicly available offensive security tools and remote access software for lateral movement and maintaining access to the environment.
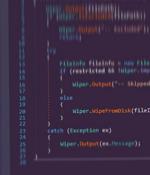
An investigation into the cyberattack targeting Iranian national media corporation, Islamic Republic of Iran Broadcasting, in late January 2022 resulted in the deployment of a wiper malware and other custom implants, as the country's national infrastructure continues to face a wave of attacks aimed at inflicting serious damage. The 10-second attack, which took place on January 27, involved the breach of state broadcaster IRIB to air pictures of Mujahedin-e-Khalq Organization leaders Maryam and Massoud Rajavi alongside a call for the assassination of the Supreme Leader Ayatollah Ali Khamenei.

An Iranian-aligned hacking group tracked as TunnelVision was spotted exploiting Log4j on VMware Horizon servers to breach corporate networks in the Middle East and the United States. Security analysts at SentinelLabs who have been tracking the activity chose that name due to the group's heavy reliance on tunneling tools, which help them hide their activities from detecting solutions.

Footage of opposition leaders calling for the assassination of Iran's Supreme Leader ran on several of the nation's state-run TV channels in late January after a state-sponsored cyber-attack on Iranian state broadcaster IRIB. The incident - one of a series of politically motivated attacks in Iran that have occurred in the last year - included the use of a wiper that potentially ties it to a previous high-profile attack on Iran's national transportation networks in July, according to researchers from Check Point Research. Though the earlier attacks have been attributed to Iran state-sponsored actor Indra, researchers believe a copycat actor was behind the IRIB attack based on the malware and tools used in the attack, they said in a report published Friday.

A "Potentially destructive actor" aligned with the government of Iran is actively exploiting the well-known Log4j vulnerability to infect unpatched VMware Horizon servers with ransomware. Cybersecurity firm SentinelOne dubbed the group "TunnelVision" owing to their heavy reliance on tunneling tools, with overlaps in tactics observed to that of a broader group tracked under the moniker Phosphorus as well as Charming Kitten and Nemesis Kitten.

An advanced persistent threat group with ties to Iran has refreshed its malware toolset to include a new backdoor dubbed Marlin as part of a long-running espionage campaign that started in April 2018. Slovak cybersecurity company ESET attributed the attacks - code named Out to Sea - to a threat actor called OilRig, while also conclusively connecting its activities to a second Iranian group tracked under the name Lyceum.
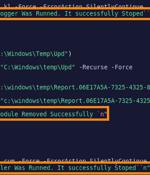
An advanced persistent threat group with links to Iran has updated its malware toolset to include a novel PowerShell-based implant called PowerLess Backdoor, according to new research published by Cybereason. The Boston-headquartered cybersecurity company attributed the malware to a hacking group known as Charming Kitten, while also calling out the backdoor's evasive PowerShell execution.
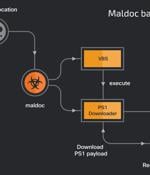
Details have emerged about a previously undocumented malware campaign undertaken by the Iranian MuddyWater advanced persistent threat group targeting Turkish private organizations and governmental institutions. "This campaign utilizes malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-based downloaders acting as initial footholds into the target's enterprise," Cisco Talos researchers Asheer Malhotra and Vitor Ventura said in a newly published report.