Security News

Apple rushed out patches for two zero-days affecting macOS and iOS Thursday, both of which are likely under active exploitation and could allow a threat actor to disrupt or access kernel activity. Apple released separate security updates for the bugs - a vulnerability affecting both macOS and iOS tracked as CVE-2022-22675 and a macOS flaw tracked as CVE-2022-22674.

Apple has released updates for its mobile and desktop operating systems to patch security holes that may well have been exploited in the wild. On Thursday, the iPhone giant issued macOS Monterey 12.3.1; iOS 15.4.1 and iPadOS 15.4.1; tvOS 15.4.1; and watchOS 8.5.1 to address vulnerabilities in its software.
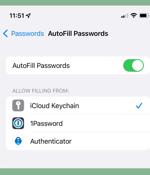
How to use AutoFill Passwords in iOS. Starting in iOS 12, Apple began allowing third-party password managers the ability to integrate directly with the operating system to offer up passwords to autofill for users in Safari and supported third-party apps. The majority of password managers that support iOS will implement the Apple Password API, which is a built-in iOS API that Apple provides to ensure a streamlined process when auto-filling passwords throughout the system in Safari and third-party apps.

Mobile security company Zimperium has released its annual mobile threat report where security trends and discoveries in the year that passed lay the groundwork for predicting what's coming in 2022. In 2021, actors focused more on remote workforce or on-premise mobile devices, leading to increased malicious network scans and man-in-the-middle attacks.
How to add notes to iCloud passwords in macOS 12.3 and iOS 15.4. Now, with iOS 15.4 and macOS 12.3, Apple has added another feature to iCloud Keychain: Notes.

iOS users: Patch now to avoid falling prey to this WebKit vulnerability. iOS users may have noticed an unexpected software update on their devices yesterday, and Apple is urging everyone to install that update immediately to avoid falling prey to a use-after-free vulnerability that could allow an attacker to execute arbitrary code on a victim's device.

Another month, another zero-day exploited in the wild that has been fixed by Apple. Apple fixed it in iOS 15.3.1 and iPadOS 15.3.1, macOS Monterey 12.2.1, and Safari 15.3.

Apple on Thursday released security updates for iOS, iPadOS, macOS, and Safari to address a new WebKit flaw that it said may have been actively exploited in the wild, making it the company's third zero-day patch since the start of the year. Tracked as CVE-2022-22620, the issue concerns a use-after-free vulnerability in the WebKit component that powers the Safari web browser and could be exploited by a piece of specially crafted web content to gain arbitrary code execution.

Microsoft says threat and vulnerability management support for Android and iOS has reached general availability in Microsoft Defender for Endpoint, the company's enterprise endpoint security platform."Threat and vulnerability management in Microsoft Defender for Endpoint continuously monitors and identifies impacted devices, assesses associated risks in the environment, and provides intelligent prioritization and integrated workflows to seamlessly remediate vulnerabilities."

Tracked as CVE-2022-22587, the vulnerability relates to a memory corruption issue in the IOMobileFrameBuffer component that could be abused by a malicious application to execute arbitrary code with kernel privileges. The iPhone maker said it's "Aware of a report that this issue may have been actively exploited," adding it addressed the issue with improved input validation.