Security News

CVE-2023-45249, a critical vulnerability affecting older versions of Acronis Cyber Infrastructure, is being exploited by attackers. Acronis Cyber Infrastructure is an IT infrastructure solution that provides storage, compute, and network resources.

Acronis warned customers to patch a critical Cyber Infrastructure security flaw that lets attackers bypass authentication on vulnerable servers using default credentials. Acronis Cyber Protect is a unified multi-tenant platform that combines remote endpoint management, backup, and virtualization capabilities and helps run disaster recovery workloads and store enterprise backup data securely.

BIND 9.20, a stable branch suitable for production use, has been released. In BIND 9.16, the developers introduced a new networking manager using libuv as an asynchronous event handler on top of the existing application infrastructure.

Cybersecurity researchers have discovered what they say is the ninth Industrial Control Systems (ICS)-focused malware that has been used in a disruptive cyber attack targeting an energy company in...

Yuliya Vladimirovna Pankratova and Denis Olegovich Degtyarenko, named by the US government as CARR's leader and attacker-in-chief respectively, were designated for their alleged roles in attacks on US critical national infrastructure. Despite much of CARR's work since its inception in 2022 revolving around what the US Department of the Treasury describes as "Low-impact, unsophisticated DDoS attacks in Ukraine," the group was blamed for various attacks on US and European water facilities earlier this year.

Costs associated with ransomware attacks on critical national infrastructure organizations skyrocketed in the past year. There's a good chance that the numbers would be skewed if 100 percent of the total CNI ransomware victims polled were entirely transparent with their figures.

Threat actors with suspected ties to China and North Korea have been linked to ransomware and data encryption attacks targeting government and critical infrastructure sectors across the world...
Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial intelligence (AI) infrastructure platform that could be exploited to achieve remote...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
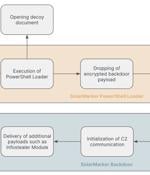
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from...