Security News

Tata Power Company Limited, India's largest integrated power company, on Friday confirmed it was targeted by a cyberattack. The intrusion on IT infrastructure impacted "Some of its IT systems," the company said in a filing with the National Stock Exchange of India.

The X-Force report pulls data from IBM's threat visibility, including X-Force Threat Intelligence data, hundreds of penetration tests, incident response engagements, and data provided by report contributor Intezer between July 2021 and June 2022. Cloud vulnerabilities are on the rise - Amid a sixfold increase in new cloud vulnerabilities over the past six years, 26% of cloud compromises that X-Force responded to were caused by attackers exploiting unpatched vulnerabilities, becoming the most common entry point observed.

The Ukrainian government on Monday warned of "Massive cyberattacks" by Russia targeting critical infrastructure facilities located in the country and that of its allies. The attacks are said to be targeting the energy sector, the Main Directorate of Intelligence of the Ministry of Defense of Ukraine said.

Russia plans to conduct "Massive cyberattacks" on Ukraine and its allies' critical infrastructure and energy sector, according to Kyiv. "The occupiers are preparing massive cyber attacks on critical infrastructure facilities of Ukraine and its allies," according to a statement from Ukraine's Defense Ministry issued on Monday.

The National Security Agency and CISA have issued guidance on how to secure operational technology and industrial control systems part of U.S. critical infrastructure.The advisory also "Notes the increasing threats to OT and ICS assets that operate, control, and monitor day-to-day critical infrastructure and industrial processes. OT/ICS designs are publicly available, as are a wealth of tools to exploit IT and OT systems."
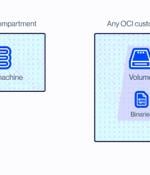
Researchers have disclosed a new severe Oracle Cloud Infrastructure vulnerability that could be exploited by users to access the virtual disks of other Oracle customers. "Each virtual disk in Oracle's cloud has a unique identifier called OCID," Shir Tamari, head of research at Wiz, said in a series of tweets.

Several bills totaling $15.6 billion are making their way through the House for the 2023 fiscal year. While $11.2 billion will go to the Department of Defense, $2.9 billion will be allocated to the Cyber Security and Infrastructure Security Agency.

A recent research found an increase in attacks across all the most targeted industries and organizations, including education, healthcare and finance. Attacks on critical infrastructure in particular have quadrupled.

83% of educational organizations confirmed they store sensitive data in the cloud. With educators and students constantly sharing that information, they are more concerned about insider threats than other industries.

A global research commissioned by Cohesity reveals that nearly half of respondents say their company depends on outdated, legacy backup and recovery infrastructure to manage and protect their data. This Help Net Security video showcases that organizations are still relying on outdated infrastructure to protect their data.