Security News

Data you don't control is open to causing you harm. The fact that nearly everyone in the US apparently likes "Instant gratification convenience over their long term security" suggests they have not yet had a piece ripped out of them.

Microsoft says Storm-0558 Chinese hackers stole a signing key used to breach government email accounts from a Windows crash dump after compromising a Microsoft engineer's corporate account. While investigating Storm-0558's attack, Microsoft found that the MSA key was leaked into a crash dump after a consumer signing system crashed in April 2021.

Online cryptocurrency casino Stake.com announced that its ETH/BSC hot wallets had been compromised to perform unauthorized transactions, with over $40 million in crypto reportedly stolen. The threat group was linked to the theft of $35 million from Atomic Wallet in June, $60 million from Alphapo in July, and another $37.3 million from CoinsPaid also in July.

Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary code, and potentially take over servers. MinIO is an open-source object storage service offering compatibility with Amazon S3 and the ability to store unstructured data, logs, backups, and container images of up to 50TB in size.

The attackers' goal was to hijack highly-privileged Okta Super Administrator accounts to access and abuse identity federation features that allowed impersonating users from the compromised organization. After a successful compromise of a Super Admin account, the threat actor used anonymizing proxy services, a fresh IP address, and a new device.
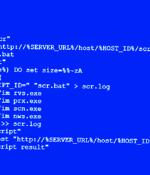
An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance object storage system to achieve unauthorized code execution on affected servers. Cybersecurity and incident response firm Security Joes said the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.

Forever 21 clothing and accessories retailer is sending data breach notifications to more than half a million individuals who had their personal information exposed to network intruders.The investigation revealed that hackers had intermittent access to Forever 21 systems between January and March this year and leveraged this access to steal data.

North Korean state-sponsored hackers have uploaded malicious packages to the PyPI repository, camouflaging one of them as a VMware vSphere connector module named vConnector. The packages were uploaded at the beginning of August, with one named VMConnect targeting IT professionals seeking virtualization tools.

North Korean state-sponsored hackers are behind the VMConnect campaign that uploaded to the PyPI repository malicious packages, one of them mimicking the VMware vSphere connector module vConnector. A report today from ReversingLabs, a software supply chain security company, attributes the campaign to Labyrinth Chollima, a subgroup of North Korean Lazarus hackers.

Hackers working for the Main Directorate of the General Staff of the Armed Forces of the Russian Federation, more commonly known as the GRU, have been targeting Android devices in Ukraine with a new malicious framework named 'Infamous Chisel. The malware was first highlighted in a warning from the Ukrainian Security Service earlier this month about efforts from the Sandworm hacking group to penetrate military command systems.