Security News

Hackers are actively exploiting a high-severity vulnerability in Openfire messaging servers to encrypt servers with ransomware and deploy cryptominers. Although Openfire fixed the issue with versions 4.6.8, 4.7.5, and 4.8.0, released in May 2023, VulnCheck reported that by mid-August 2023, over 3,000 Openfire servers were still running a vulnerable version.
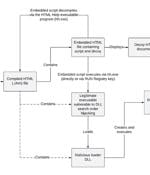
A "multi-year" Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and government organizations. Recorded Future's Insikt Group, which is...

Group-IB analysts attribute with various degrees of confidence ShadowSyndicate's use of the Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play ransomware in breaches since July 2022. Based on their findings, researchers believe that the threat actor could be an initial access broker, although evidence suggests that ShadowSyndicate is an affiliate to multiple ransomware operations.

A stealthy advanced persistent threat tracked as Gelsemium was observed in attacks targeting a Southeast Asian government that spanned six months between 2022 and 2023. Gelsemium is a cyberespionage group operational since 2014, targeting government, education, and electronic manufacturers in East Asia and the Middle East.

The Government of British Overseas Territory Bermuda has linked a cyberattack affecting all its departments' IT systems since Thursday to hackers based out of Russia. "The public is advised that the Government Is currently experiencing internet/email and phone service interruptions. All Departments are impacted," the Bermuda Government said.

Security researchers discovered a multi-step information stealing campaign where hackers breach the systems of hotels, booking sites, and travel agencies and then use their access to go after financial data belonging to customers. "After the infostealer is executed on the original target, the attacker can access messaging with legitimate customers" - Shiran Guez, information security senior manager at Akamai.

A previously unknown threat actor dubbed 'Sandman' targets telecommunication service providers in the Middle East, Western Europe, and South Asia, using a modular info-stealing malware named 'LuaDream. SandMan has been seen deploying a new modular malware named 'LuaDream' in attacks using DLL hijacking on targeted systems.
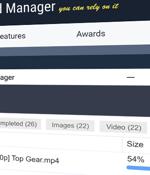
The maintainers of Free Download Manager (FDM) have acknowledged a security incident dating back to 2020 that led to its website being used to distribute malicious Linux software. "It appears that...

The International Criminal Court disclosed a cyberattack on Tuesday after discovering last week that its systems had been breached. "At the end of last week, the International Criminal Court's services detected anomalous activity affecting its information systems," the ICC said.

New malware named HTTPSnoop and PipeSnoop are used in cyberattacks on telecommunication service providers in the Middle East, allowing threat actors to remotely execute commands on infected devices. The HTTPSnoop malware interfaces with Windows HTTP kernel drivers and devices to execute content on the infected endpoint based on specific HTTP(S) URLs, and the PipeSnoop accepts and executes arbitrary shellcode from a named pipe.