Security News

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Kurtaj who is 18 years of age and autistic is among the primary Lapsus$ threat actors, and was involved in the leak of assets associated with the video game, Grand Theft Auto VI. Sentenced to life in a 'secure hospital'. Arion Kurtaj, a member of the Lapsus$ cybercrime group, was sentenced indefinitely to a "Secure hospital" by a British judge, according to a BBC report.

Microsoft says the APT33 Iranian cyber-espionage group is using recently discovered FalseFont backdoor malware to attack defense contractors worldwide. "Microsoft has observed the Iranian nation-state actor Peach Sandstorm attempting to deliver a newly developed backdoor named FalseFont to individuals working for organizations in the Defense Industrial Base sector," the company said.

Attackers are weaponizing an old Microsoft Office vulnerability as part of phishing campaigns to distribute a strain of malware called Agent Tesla. The infection chains leverage decoy Excel...
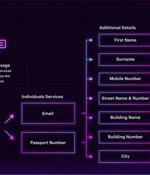
The Chinese-speaking threat actors behind Smishing Triad have been observed masquerading as the United Arab Emirates Federal Authority for Identity and Citizenship to send malicious SMS messages...
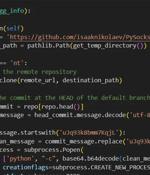
Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages. "Malware...

The Iranian nation-state actor known as MuddyWater has leveraged a newly discovered command-and-control (C2) framework called MuddyC2Go in its attacks on the telecommunications sector in Egypt,...

Russian state-sponsored hackers have been exploiting CVE-2023-42793 to target unpatched, internet-facing JetBrains TeamCity servers since September 2023, US, UK and Polish cybersecurity and law enforcement authorities have warned. As they noted, this time around, "The victim types do not fit into any sort of pattern or trend, aside from having an unpatched, Internet-reachable JetBrains TeamCity server."
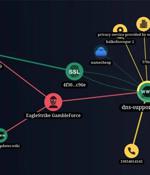
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the Asia-Pacific (APAC) region since at least...

CISA and partner cybersecurity agencies and intelligence services warned that the APT29 hacking group linked to Russia's Foreign Intelligence Service has been targeting unpatched TeamCity servers in widespread attacks since September 2023. Security researchers at nonprofit internet security outfit Shadowserver Foundation are tracking almost 800 unpatched TeamCity servers that are vulnerable to attacks.