Security News

Threat actors are attempting to actively exploit a critical security flaw in the WP‑Automatic plugin for WordPress that could allow site takeovers. The shortcoming, tracked as CVE-2024-27956,...

A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data collection on target environments. Cisco Talos, which dubbed...

A state-sponsored threat actor has managed to compromise Cisco Adaptive Security Appliances used on government networks across the globe and use two zero-day vulnerabilities to install backdoors on them, Cisco Talos researchers have shared on Wednesday."On a compromised ASA, the attackers submit shellcode via the host-scan-reply field, which is then parsed by the Line Dancer implant. The host-scan-reply field, typically used in later parts of the SSL VPN session establishment process, is processed by ASA devices configured for SSL VPN, IPsec IKEv2 VPN with 'client-services' or HTTPS management access," the researchers explained.

Cisco warned today that a state-backed hacking group has been exploiting two zero-day vulnerabilities in Adaptive Security Appliance and Firepower Threat Defense firewalls since November 2023 to breach government networks worldwide. The hackers, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, began infiltrating vulnerable edge devices in early November 2023 in a cyber-espionage campaign tracked as ArcaneDoor.

North Korean hackers have been exploiting the updating mechanism of the eScan antivirus to plant backdoors on big corporate networks and deliver cryptocurrency miners through GuptiMiner malware. Researchers describe GuptiMiner as "a highly sophisticated threat" that can perform DNS requests to the attacker's DNS servers, extract payloads from images, sign its payloads, and perform DLL sideloading.

For nearly four years and perhaps even longer, Forest Blizzard has been using a custom tool that exploits a specific vulnerability in Windows Print Spooler service. Dubbed GooseEgg, the tool is a launcher application that can spawn other applications with SYSTEM-level permissions, thus helping the hackers to perform remote code execution, install backdoors, steal credentials, and more.

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 has been using this tool to exploit the CVE-2022-38028 vulnerability "Since at least June 2020 and possibly as early as April 2019.".

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 designed this tool to target the CVE-2022-38028 vulnerability reported by the U.S. National Security Agency, which Redmond fixed during the Microsoft October 2022 Patch Tuesday.
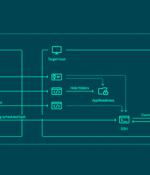
The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky...

Russian hacker group Sandworm aimed to disrupt operations at around 20 critical infrastructure facilities in Ukraine, according to a report from the Ukrainian Computer Emergency Response Team. The attacks occurred in March and in some cases the hackers were able to infiltrate the targeted network by poisoning the supply chain to deliver compromised or vulnerable software, or through the software provider's ability to access organization's systems for maintainance and technical suport.