Security News
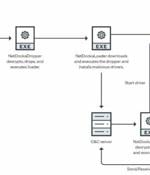
A pay-per-install malware service known as PrivateLoader has been spotted distributing a "Fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices. PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.

The U.S. Department of Treasury today sanctioned cryptocurrency mixer Blender.io used last month by the North Korean-backed Lazarus hacking group to launder funds stolen from Axie Infinity's Ronin bridge. In the wake of the attack, Sky Mavis revealed that hackers breached the Ronin bridge on March 23 to steal 173,600 Ethereum and 25.5M USDC tokens in two transactions worth $617 million at the time, the largest cryptocurrency hack in history.
A growing number of threat actors are using the ongoing Russo-Ukrainian war as a lure in various phishing and malware campaigns, even as critical infrastructure entities continue to be heavily targeted. The findings follow disclosures that a China-linked government-sponsored threat actor known as Mustang Panda may have been targeting Russian government officials with an updated version of a remote access trojan called PlugX. Another set of phishing attacks involved APT28 hackers targeting Ukrainian users with a.NET malware that's capable of stealing cookies and passwords from Chrome, Edge and Firefox browsers.

The Chinese hacking group known as 'Winnti' has been stealthily stealing intellectual property assets like patents, copyrights, trademarks, and other corporate data - all while remaining undetected by researchers and targets since 2019. Winnti establishes persistence via an encoded WebShell, by abusing the WinRM protocol for remote access, the IKEEXT and PrintNotify Windows services for DLL side-loading, or by loading a signed kernel rootkit.

Dubbed "Operation CuckooBees" by Israeli cybersecurity company Cybereason, the massive intellectual property theft operation enabled the threat actor to exfiltrate hundreds of gigabytes of information. "The attackers targeted intellectual property developed by the victims, including sensitive documents, blueprints, diagrams, formulas, and manufacturing-related proprietary data," the researchers said.
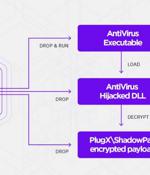
A Chinese-aligned cyberespionage group has been observed striking the telecommunication sector in Central Asia with versions of malware such as ShadowPad and PlugX. Cybersecurity firm SentinelOne tied the intrusions to an actor it tracks under the name "Moshen Dragon," with tactical overlaps between the collective and another threat group referred to as Nomad Panda. ShadowPad, labeled a "Masterpiece of privately sold malware in Chinese espionage," emerged as a successor to PlugX in 2015, even as variants of the latter have continually popped up as part of different campaigns associated with Chinese threat actors.

Threat analysts at the cybersecurity firm Mandiant have uncovered a new APT29 cyber attack once again aimed at diplomats and government agencies. APT29 is a cyber espionage group widely believed to be sponsored by the Russian Foreign Intelligence Service, the SVR. APT29 is also publicly referred to as Nobelium by Microsoft, Mandiant said.
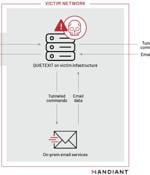
A newly discovered suspected espionage threat actor has been targeting employees focusing on mergers and acquisitions as well as large corporate transactions to facilitate bulk email collection from victim environments. Mandiant is tracking the activity cluster under the uncategorized moniker UNC3524, citing a lack of evidence linking it to an existing group.

A Russian state-sponsored threat actor has been observed targeting diplomatic and government entities as part of a series of phishing campaigns commencing on January 17, 2022. Threat intelligence and incident response firm Mandiant attributed the attacks to a hacking group tracked as APT29, with some set of the activities associated with the crew assigned the moniker Nobelium.

A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information. "The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as 'Viper,'" Cluster25 said in a report published last week.