Security News > 2022 > May > Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
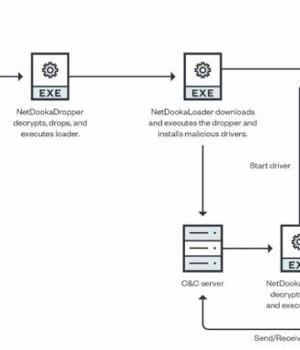
A pay-per-install malware service known as PrivateLoader has been spotted distributing a "Fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices.
PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Featuring anti-analysis techniques, PrivateLoader is written in the C++ programming language and is said to be in active development, with the downloader malware family gaining traction among multiple threat actors.
"The loader will likely continue to be updated with new features and functionality to evade detection and effectively deliver second-stage malware payloads."
The newly observed set of infections involving the NetDooka framework commences with PrivateLoader acting as a conduit to deploy a dropper component, which then decrypts and executes a loader that, in turn, retrieves another dropper from a remote server to install a full-featured trojan as well as a kernel driver.
"PPI malware services allow malware creators to easily deploy their payloads," Zahravi and Froes concluded.
News URL
https://thehackernews.com/2022/05/hackers-using-privateloader-ppi-service.html
Related news
- Hackers Exploit ConnectWise ScreenConnect Flaws to Deploy TODDLERSHARK Malware (source)
- Hackers target Docker, Hadoop, Redis, Confluence with new Golang malware (source)
- Magnet Goblin hackers use 1-day flaws to drop custom Linux malware (source)
- Hackers exploit WordPress plugin flaw to infect 3,300 sites with malware (source)
- Hackers leverage 1-day vulnerabilities to deliver custom Linux malware (source)
- Hackers abuse Windows SmartScreen flaw to drop DarkGate malware (source)
- Hackers exploit Windows SmartScreen flaw to drop DarkGate malware (source)
- Week in review: Cybersecurity job openings, hackers use 1-day flaws to drop custom Linux malware (source)
- Hackers Using Sneaky HTML Smuggling to Deliver Malware via Fake Google Sites (source)
- Russian Hackers May Have Targeted Ukrainian Telecoms with Upgraded 'AcidPour' Malware (source)