Security News

The notorious North Korean hacking group 'Lazarus' was seen installing a Windows rootkit that abuses a Dell hardware driver in a Bring Your Own Vulnerable Driver attack. ESET reports that among the tools deployed in this campaign, the most interesting is a new FudModule rootkit that abuses a BYOVD technique to exploit a vulnerability in a Dell hardware driver for the first time.

Once they've broken into an IT environment, most intruders need less than five hours to collect and steal sensitive data, according to a SANS Institute survey of more than 300 ethical hackers. More than half of respondents stated they could successfully discover an exploitable exposure in ten hours or less.

Microsoft on Friday disclosed that a single activity group in August 2022 achieved initial access and breached Exchange servers by chaining the two newly disclosed zero-day flaws in a limited set of attacks aimed at less than 10 organizations globally. "These attacks installed the Chopper web shell to facilitate hands-on-keyboard access, which the attackers used to perform Active Directory reconnaissance and data exfiltration," the Microsoft Threat Intelligence Center said in a Friday report.

The U.S. Cybersecurity and Infrastructure Security Agency on Friday added a recently disclosed critical flaw impacting Atlassian's Bitbucket Server and Data Center to the Known Exploited Vulnerabilities catalog, citing evidence of active exploitation. Tracked as CVE-2022-36804, the issue relates to a command injection vulnerability that could allow malicious actors to gain arbitrary code execution on susceptible installations by sending a specially crafted HTTP request.

The Cybersecurity and Infrastructure Security Agency has added three more security flaws to its list of bugs exploited in attacks, including a Bitbucket Server RCE and two Microsoft Exchange zero-days.While Microsoft hasn't yet released security updates to address this pair of actively exploited bugs, it shared mitigation measures requiring customers to add an IIS server blocking rule that would block attack attempts.

Germany's Bundeskriminalamt, the country's federal criminal police, carried out raids on the homes of three individuals yesterday suspected of orchestrating large-scale phishing campaigns that defrauded internet users of €4,000,000. The three men obtained money from their victims by sending them phishing emails that were clones of messages from real German banks.
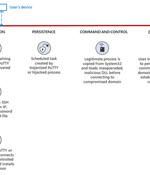
A "Highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022. Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.

Microsoft says the North Korean-sponsored Lazarus threat group is trojanizing legitimate open-source software and using it to backdoor organizations in many industry sectors, such as technology, defense, and media entertainment. The list of open-source software weaponized by Lazarus state hackers to deploy the BLINDINGCAN backdoor includes PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer.
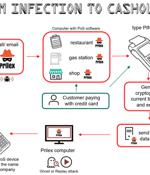
A Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to steal money by means of fraudulent transactions. "The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works," Kaspersky researchers said.

Several hacktivist groups are using Telegram and other tools to aid anti-government protests in Iran to bypass regime censorship restrictions amid ongoing unrest in the country following the death of Mahsa Amini in custody. The company said it has also witnessed sharing of proxies and open VPN servers to get around censorship and reports on the internet status in the country, with one group helping the anti-government demonstrators access social media sites.