Security News

Pwn2Own paid out almost $1 million to bug hunters at last week's consumer product hacking event in Toronto, but the prize money wasn't big enough attract attempts at cracking the iPhone or Google Pixel because miscreants can score far more from less wholesome sources. The contest planned to give away $250,000 for a successful iPhone or Google Pixel exploit, he told The Register, in an exclusive interview at the end of the four-day event.

Pwn2Own Toronto 2022 has ended with competitors earning $989,750 for 63 zero-day exploits targeting consumer products between December 6th and December 9th. During this hacking competition, 26 teams and security researchers have targeted devices in the mobile phones, home automation hubs, printers, wireless routers, network-attached storage, and smart speakers categories, all up-to-date and in their default configuration. The STAR Labs team was the first to exploit a zero-day in Samsung's flagship device by executing an improper input validation attack on their third attempt, earning $50,000 and 5 Master of Pwn points.

U.S. healthcare organizations could be in the crosshairs of a new cyberthreat collective dubbed Royal. The warning from HHS's Health Sector Cybersecurity Coordination Center identified the relatively new group as perps behind several attacks first appearing in September 2022 against Healthcare and Public Healthcare targets.
The Iran-linked MuddyWater threat actor has been observed targeting several countries in the Middle East as well as Central and West Asia as part of a new spear-phishing activity. "The campaign...
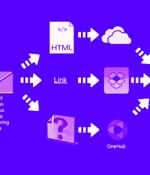
Researchers have shed light on a new hybrid malware campaign targeting both Android and Windows operating systems in a bid to expand its pool of victims. The attacks entail the use of different malware such as ERMAC, Erbium, Aurora, and Laplas, according to a ThreatFabric report shared with The Hacker News.

An Internet Explorer zero-day vulnerability was actively exploited by a North Korean threat actor to target South Korean users by capitalizing on the recent Itaewon Halloween crowd crush to trick users into downloading malware. "The group has historically focused their targeting on South Korean users, North Korean defectors, policy makers, journalists, and human rights activists," TAG said in a Thursday analysis.
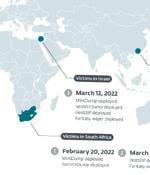
An Iranian advanced persistent threat actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong. The wiper, codenamed Fantasy by ESET, is believed to have been delivered via a supply chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.

The Iranian Agrius APT hacking group is using a new 'Fantasy' data wiper in supply-chain attacks impacting organizations in Israel, Hong Kong, and South Africa. In this campaign, Agrius used a new wiper named 'Fantasy' hidden inside a software suite created by an Israeli vendor.

Google's Threat Analysis Group revealed today that a group of North Korean hackers tracked as APT37 exploited a previously unknown Internet Explorer vulnerability to infect South Korean targets with malware. Once opened on the victims' devices, the document would deliver an unknown payload after downloading a rich text file remote template that would render remote HTML using Internet Explorer.

The China-linked nation-state hacking group referred to as Mustang Panda is using lures related to the ongoing Russo-Ukrainian War to attack entities in Europe and the Asia Pacific. Mustang Panda is a prolific cyber-espionage group from China that's also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.