Security News

The Main Intelligence Directorate of Ukraine's Ministry of Defense claims that pro-Ukrainian hacktivists breached the Russian Center for Space Hydrometeorology, aka "Planeta", and wiped 2 petabytes of data. Planeta is a state research center using space satellite data and ground sources like radars and stations to provide information and accurate predictions about weather, climate, natural disasters, extreme phenomena, and volcanic monitoring.

Some organizations victimized by the Royal and Akira ransomware gangs have been targeted by a threat actor posing as a security researcher who promised to hack back the original attacker and delete stolen victim data. Cybersecurity company Arctic Wolf says it has investigated "Several cases" where victims of the two ransomware groups that paid a ransom were approached by a threat actor claiming to be an ethical hacker or security researcher with a deep understanding of the field.
American cybersecurity firm and Google Cloud subsidiary Mandiant had its X (formerly Twitter) account compromised for more than six hours by an unknown attacker to propagate a cryptocurrency scam....

Orbit Chain has experienced a security breach that has resulted in a loss of $86 million in cryptocurrency, particularly Ether, Dai, Tether, and USD Coin. Orbit Chain is a blockchain platform designed to function as a multi-asset hub, supporting interoperability between various blockchains, decentralized applications, and services.
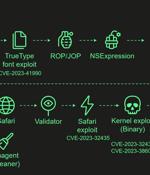
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections...

The source code for Grand Theft Auto 5 was reportedly leaked on Christmas Eve, a little over a year after the Lapsus$ threat actors hacked Rockstar games and stole corporate data. Links to download the source code were shared on numerous channels, including Discord, a dark web website, and a Telegram channel that the hackers previously used to leak stolen Rockstar data.

Following an investigation into the impact of the security breach, Xfinity discovered on November 16 that the attackers also exfiltrated data belonging to an undisclosed number of customers from its systems. "After additional review of the affected systems and data, Xfinity concluded on December 6, 2023, that the customer information in scope included usernames and hashed passwords; for some customers, other information may also have been included, such as names, contact information, last four digits of social security numbers, dates of birth and/or secret questions and answers. However, the data analysis is continuing," the company said.

Kraft Heinz has confirmed that their systems are operating normally and that there is no evidence they were breached after an extortion group listed them on a data leak site. In a post to Snatch extortion group's data leak site dated August 16th, but not made visible until today, the threat actors claim that they breached Kraft Heinz.

Webinar Whether you are considering a career in cyber security or you already work in the industry, the 2023 SANS Holiday Hack Challenge is a great way of combining festive fun and learning. Who knows, the skills you acquire this holiday season might even help you foil a nefarious hacker at Yuletide next year.

The government of the United Kingdom has issued a strongly worded denial of a report that the Sellafield nuclear complex has been compromised by malware for years. The report, appearing in The Guardian, claimed that the controversial complex was hacked by "Cyber groups closely linked to Russia and China," with the infection detected in 2015 but perhaps present before that year.