Security News

GitHub will require all users who contribute code on the platform to enable two-factor authentication as an additional protection measure on their accounts by the end of 2023. Imposing 2FA as a mandatory measure for all GitHub accounts will make the platform a safer space where users can feel more confident about the quality of the code they download from repositories.

GitHub is rolling out support for the free scanning of exposed secrets to all public repositories on its code hosting platform. Secret scanning is a security option that organizations can enable for additional repository scanning to detect accidental exposure of known types of secrets.

The subgroup of an Iranian nation-state group known as Nemesis Kitten has been attributed as behind a previously undocumented custom malware dubbed Drokbk that uses GitHub as a dead drop resolver...

GitHub is offering a scheme for security researchers to privately report vulnerabilities found in public repositories. Being able to privately report code flaws is important to researchers who are often left with choices that can lead to more security problems, GitHub said in a blog post.

Programmer and lawyer Matthew Butterick has sued Microsoft, GitHub, and OpenAI, alleging that GitHub's Copilot violates the terms of open-source licenses and infringes the rights of programmers. GitHub Copilot, released in June 2022, is an AI-based programming aid that uses OpenAI Codex to generate real-time source code and function recommendations in Visual Studio.

File hosting service Dropbox on Tuesday disclosed that it was the victim of a phishing campaign that allowed unidentified threat actors to gain unauthorized access to 130 of its source code repositories on GitHub."These repositories included our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the security team," the company revealed in an advisory.

Dropbox has said it was successfully phished, resulting in someone copying 130 of its private GitHub code repositories and swiping some of its secret API credentials. GitHub let Dropbox know the next day, and the cloud storage outfit investigated.

Dropbox disclosed a security breach after threat actors stole 130 code repositories after gaining access to one of its GitHub accounts using employee credentials stolen in a phishing attack. "To date, our investigation has found that the code accessed by this threat actor contained some credentials-primarily, API keys-used by Dropbox developers," Dropbox revealed on Tuesday.
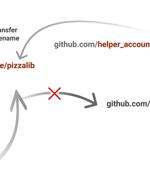
Cloud-based repository hosting service GitHub has addressed a high-severity security flaw that could have been exploited to create malicious repositories and mount supply chain attacks. The RepoJacking technique, disclosed by Checkmarx, entails a bypass of a protection mechanism called popular repository namespace retirement, which aims to prevent developers from pulling unsafe repositories with the same name.

A stealthy cryptocurrency mining operation has been spotted using thousands of free accounts on GitHub, Heroku and other DevOps outfits to craft digital tokens. Sysdig estimated each of those 30 free GitHub accounts cost the Microsoft-owned giant $15 per month, and the free tier accounts from Heroku, Buddy and others cost providers between $7 and $10 per month.