Security News > 2022 > October > GitHub Repojacking Bug Could've Allowed Attackers to Takeover Other Users' Repositories
Cloud-based repository hosting service GitHub has addressed a high-severity security flaw that could have been exploited to create malicious repositories and mount supply chain attacks.
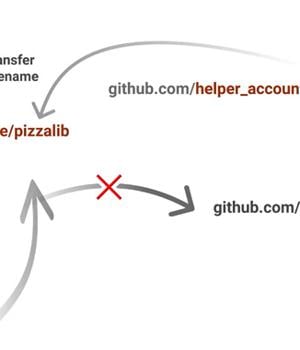
The RepoJacking technique, disclosed by Checkmarx, entails a bypass of a protection mechanism called popular repository namespace retirement, which aims to prevent developers from pulling unsafe repositories with the same name.
While Microsoft's countermeasure "Retire[s] the namespace of any open source project that had more than 100 clones in the week leading up to the owner's account being renamed or deleted," Checkmarx found that this can be circumvented through the "Repository transfer" feature.
In other words, the attack hinges on the quirk that GitHub only considers as retired the namespace, i.e., the combination of username and repository name, permitting a bad actor to reuse the repository name in conjunction with an arbitrary username.
A successful exploitation could have effectively allowed attackers to push poisoned repositories, putting renamed usernames at risk of being a victim of supply chain attacks.
"If not explicitly tended, all renamed usernames on GitHub were vulnerable to this flaw, including over 10,000 packages on the Go, Swift, and Packagist package managers," Checkmarx researcher Aviad Gershon said.
News URL
https://thehackernews.com/2022/10/github-repojacking-bug-couldve-allowed.html