Security News

The U.S. Federal Bureau of Investigation is warning that Barracuda Networks Email Security Gateway appliances patched against a recently disclosed critical flaw continue to be at risk of potential compromise from suspected Chinese hacking groups. It also deemed the fixes as "Ineffective" and that it "Continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit."

Administrators of Citrix NetScaler ADC and Gateway appliances should check for evidence of installed webshells even if they implemented fixes for CVE-2023-3519 quickly: A recent internet scan by Fox-IT researchers has revealed over 1,800 backdoored NetScaler devices, 69% of which have been patched for the flaw. CVE-2023-3519 exploited to drop webshells on NetScaler devices.

Mandiant has released a scanner to check if a Citrix NetScaler Application Delivery Controller or NetScaler Gateway Appliance was compromised in widespread attacks exploiting the CVE-2023-3519 vulnerability. The critical CVE-2023-3519 Citrix flaw was discovered in mid-July 2023 as a zero-day, with hackers actively exploiting it to execute code remotely without authentication on vulnerable devices.

Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors to deploy web shells, according to the Shadowserver Foundation. The non-profit said the attacks take advantage of CVE-2023-3519, a critical code injection vulnerability that could lead to unauthenticated remote code execution.
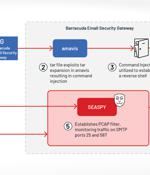
The U.S. Cybersecurity and Infrastructure Security Agency on Friday disclosed details of a "Novel persistent backdoor" called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway appliances. The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868, which allows for remote command injection.

The U.S. Cybersecurity and Infrastructure Security Agency issued an advisory on Thursday warning that the newly disclosed critical security flaw in Citrix NetScaler Application Delivery Controller and Gateway devices is being abused to drop web shells on vulnerable systems. "In June 2023, threat actors exploited this vulnerability as a zero-day to drop a web shell on a critical infrastructure organization's non-production environment NetScaler ADC appliance," the agency said.

Citrix is alerting users of a critical security flaw in NetScaler Application Delivery Controller and Gateway that it said is being actively exploited in the wild.The company did not give further details on the flaw tied to CVE-2023-3519 other than to say that exploits for the flaw have been observed on "Unmitigated appliances." However, successful exploitation requires the device to be configured as a Gateway or authorization and accounting virtual server.

Citrix today is alerting customers of a critical-severity vulnerability in NetScaler ADC and NetScaler Gateway that already has exploits in the wild, and "Strongly urges" to install updated versions without delay. Formerly Citrix ADC and Citrix Gateway, the two NetScaler products received new versions today to mitigate a set of three vulnerabilities.

Citrix today is alerting customers of a critical-severity vulnerability in NetScaler ADC and NetScaler Gateway that already has exploits in the wild, and "Strongly urges" to install updated versions without delay. Formerly Citrix ADC and Citrix Gateway, the two NetScaler products received new versions today to mitigate a set of three vulnerabilities.

Citrix today is alerting customers of a critical-severity vulnerability in NetScaler ADC and NetScaler Gateway that already has exploits in the wild, and "Strongly urges" to install updated versions without delay. Formerly Citrix ADC and Citrix Gateway, the two NetScaler products received new versions today to mitigate a set of three vulnerabilities.