Security News

The Linux Foundation, in collaboration with OpenSSF and Linux Foundation Education, has released the Cybersecurity Skills Framework, a global reference guide that helps organizations identify and...

Malicious activity in the ICT environment is growing. However, a non-technical audience often struggle to understand these threats, either because technical explanations are too complex or because...
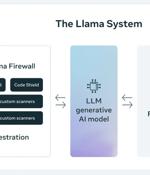
Meta on Tuesday announced LlamaFirewall, an open-source framework designed to secure artificial intelligence (AI) systems against emerging cyber risks such as prompt injection, jailbreaks, and...

Villain is an open-source Stage 0/1 command-and-control (C2) framework designed to manage multiple reverse TCP and HoaxShell-based shells. Beyond simply handling connections, Villain enhances...

Threat actors are likely exploiting a new vulnerability in SAP NetWeaver to upload JSP web shells with the goal of facilitating unauthorized file uploads and code execution. "The exploitation is...

BlueToolkit is an open-source tool that helps find security flaws in Bluetooth Classic devices. It runs known and custom exploits to test if a device is vulnerable. Right now, it includes 43...
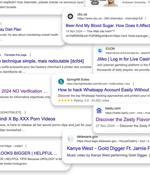
A cross-site scripting (XSS) vulnerability in a virtual tour framework has been weaponized by malicious actors to inject malicious scripts across hundreds of websites with the goal of manipulating...

Beelzebub is an open-source honeypot framework engineered to create a secure environment for detecting and analyzing cyber threats. It features a low-code design for seamless deployment and...

BloodyAD is an open-source Active Directory privilege escalation framework that uses specialized LDAP calls to interact with domain controllers. It enables various privilege escalation techniques...

A high-severity security flaw has been disclosed in Meta's Llama large language model (LLM) framework that, if successfully exploited, could allow an attacker to execute arbitrary code on the...