Security News

Ongoing attacks are targeting an Unauthenticated Stored Cross-Site Scripting vulnerability in a WordPress cookie consent plugin named Beautiful Cookie Consent Banner with more than 40,000 active installs. WordPress security company Defiant, which spotted the attacks, says the vulnerability in question also allows unauthenticated attackers to create rogue admin accounts on WordPress websites running unpatched plugin versions.

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services Elastic Compute Cloud instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil.

A proof-of-concept has been made available for a security flaw impacting the KeePass password manager that could be exploited to recover a victim's master password in cleartext under specific circumstances. "Apart from the first password character, it is mostly able to recover the password in plaintext," security researcher "Vdhoney," who discovered the flaw and devised a PoC, said.

The popular KeePass password manager is vulnerable to extracting the master password from the application's memory, allowing attackers who compromise a device to retrieve the password even with the database is locked. This master password encrypts the KeePass password database, preventing it from being opened or read without first entering the password.

Cisco warned customers today of four critical remote code execution vulnerabilities with public exploit code affecting multiple Small Business Series Switches."The vulnerabilities are not dependent on one another. Exploitation of one of the vulnerabilities is not required to exploit another vulnerability," Cisco explained.

These apps have popped up in the Google Play and Apple App Store. "Scammers have and always will use the latest trends or technology to line their pockets. ChatGPT is no exception. With interest in AI and chatbots arguably at an all-time high, users are turning to the Apple App and Google Play Stores to download anything that resembles ChatGPT," said Sean Gallagher, principal threat researcher, Sophos.
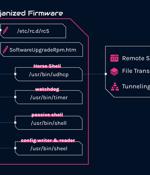
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023. An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.

Hackers are actively exploiting a recently fixed vulnerability in the WordPress Advanced Custom Fields plugin roughly 24 hours after a proof-of-concept exploit was made public. The vulnerability in question is CVE-2023-30777, a high-severity reflected cross-site scripting flaw that allows unauthenticated attackers to steal sensitive information and escalate their privileges on impacted WordPress sites.
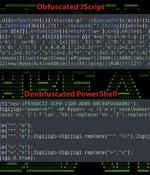
Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare clinics located in Germany.

A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices. While the malware is known to weaponize remote code execution flaws in GitLab and Lilin DVR for propagation, the addition of CVE-2023-25717 shows that Andoryu is actively expanding its exploit arsenal to ensnare more devices into the botnet.