Security News

Technical specifics and a proof-of-concept (PoC) exploit have been made available for a recently disclosed critical security flaw in Progress Software OpenEdge Authentication Gateway and...

A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing...

Hackers are breaching WordPress sites by exploiting a vulnerability in outdated versions of the Popup Builder plugin, infecting over 3,300 websites with malicious code. Sucuri says the exact actions of the code may vary, but the primary purpose of the injections appears to be redirecting visitors of infected sites to malicious destinations such as phishing pages and malware-dropping sites.

Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to...

North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a new malware called TODDLERSHARK. According to a report shared by Kroll with...

A critical vulnerability in the TeamCity On-Premises CI/CD solution from JetBrains can let a remote unauthenticated attacker take control of the server with administrative permissions. "Compromising a TeamCity server allows an attacker full control over all TeamCity projects, builds, agents and artifacts, and as such is a suitable vector to position an attacker to perform a supply chain attack" - Rapid7.
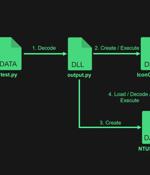
The notorious North Korean state-backed hacking group Lazarus uploaded four packages to the Python Package Index (PyPI) repository with the goal of infecting developer systems with malware. The...

Threat actors are exploiting a CMS editor discontinued 14 years ago to compromise education and government entities worldwide to poison search results with malicious sites or scams. Search engine crawlers index the redirects and list them on Google Search results, making them an effective strategy for SEO poisoning campaigns, leveraging a trusted domain to rank malicious URLs higher for specific queries.

CISA has assigned CVE-2024-1708 and CVE-2024-1709 identifiers to the the two security issues, which the vendor assessed as a maximum severity authentication bypass and a high-severity path traversal flaw that impact ScreenConnect servers 23.9.7 and earlier. Threat actors have compromised multiple ScreenConnect accounts, as confirmed by the company in an update to its advisory, based on incident response investigations.

Hackers are actively exploiting a critical remote code execution flaw impacting the Brick Builder Theme to run malicious PHP code on vulnerable sites. The Bricks Builder Theme is a premium WordPress theme described as an innovative, community-driven visual site builder.