Security News

RansomLord is an open-source tool that automates the creation of PE files, which are used to exploit ransomware pre-encryption. "I created RansomLord to demonstrate ransomware is not invincible, has vulnerabilities and its developers make mistakes and can write bad code just like everyone else," hyp3rlinx, developer of RansomLord, told Help Net Security.

Security researchers have released a proof-of-concept exploit for a maximum-severity vulnerability in Fortinet's security information and event management solution, which was patched in February.On Tuesday, over three months after Fortinet released security updates to patch this security flaw, Horizon3's Attack Team shared a proof-of-concept exploit and published a technical deep-dive.

Google fixes yet another Chrome zero-day exploited in the wildFor the eighth time this year, Google has released an emergency update for its Chrome browser that fixes a zero-day vulnerability with an in-the-wild exploit. GitHub fixes maximum severity Enterprise Server auth bypass bugA critical, 10-out-of-10 vulnerability allowing unrestricted access to vulnerable GitHub Enterprise Server instances has been fixed by Microsoft-owned GitHub.

Google on Thursday rolled out fixes to address a high-severity security flaw in its Chrome browser that it said has been exploited in the wild. Assigned the CVE identifier CVE-2024-5274, the...

Ransomware attacks targeting VMware ESXi infrastructure following an established pattern regardless of the file-encrypting malware deployed. "Virtualization platforms are a core component of...
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what's called a Bring...

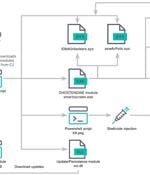
A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. "The VBScript and PowerShell...

The above bugs impact QTS, the NAS operating system on QNAP devices, QuTScloud, the VM-optimized version of QTS, and QTS hero, a specialized version focused on high performance. QNAP has addressed CVE-2023-50361 through CVE-2023-50364 in a security update released in April 2024, in versions QTS 5.1.6.2722 build 20240402 and later, and QuTS hero h5.1.6.2734 build 20240414 and later.

Technical details about and a proof-of-concept (PoC) exploit for CVE-2024-22026, a privilege escalation bug affecting Ivanti EPMM, has been released by the vulnerability’s reporter. About...

A "multi-faceted campaign" has been observed abusing legitimate services like GitHub and FileZilla to deliver an array of stealer malware and banking trojans such as Atomic (aka AMOS), Vidar,...