Security News
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed a new set of cyber attacks targeting Ukrainian institutions with information-stealing malware. The activity is aimed at...
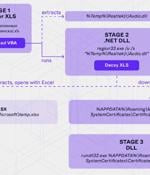
Opposition activists in Belarus as well as Ukrainian military and government organizations are the target of a new campaign that employs malware-laced Microsoft Excel documents as lures to deliver...

Microsoft has denied claims that it uses Microsoft 365 apps (including Word, Excel, and PowerPoint) to collect data to train the company's artificial intelligence (AI) models. [...]

Cybersecurity researchers have discovered a new phishing campaign that spreads a new fileless variant of known commercial malware called Remcos RAT. Remcos RAT "provides purchases with a wide...
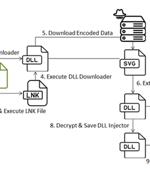
A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per...

Security teams are hiding an embarrassing secret from the outside world: despite their position at the vanguard of technology, security risks and threats, their actual war plans are managed on spreadsheets. Using these spreadsheets requires security operations to chase down every team in their organization for input on everything from the mapping of exceptions and end-of-life of machines to tracking hardware and operating systems.

The U.S. Cybersecurity and Infrastructure Security Agency has added two vulnerabilities to the Known Exploited Vulnerabilities catalog, a recently patched flaw in Google Chrome and a bug affecting an open-source Perl library for reading information in an Excel file called Spreadsheet::ParseExcel. Spreadsheet::ParseExcel RCE. The first issue that CISA added to its Known Exploited Vulnerabilities is CVE-2023-7101, a remote code execution vulnerability that affects versions 0.65 and older of the Spreadsheet::ParseExcel library.

Attackers are weaponizing an old Microsoft Office vulnerability as part of phishing campaigns to distribute a strain of malware called Agent Tesla. The infection chains leverage decoy Excel...

Even if you join the Microsoft 365 Insiders Beta channel to test the new feature, there is no guarantee that Python in Excel will be available, as Microsoft is rolling it out slowly to test the feature. The new Python in Excel feature brings a new 'PY' function that allows users to embed Python code directly in a cell to be executed like any macro or regular Excel function.

In this detailed article about academic plagiarism are some interesting details about how to do data forensics on Excel files. It really needs the graphics to understand, so see the description at the link.