Security News

A phishing campaign that security researchers named SmugX and attributed to a Chinese threat actor has been targeting embassies and foreign affairs ministries in the UK, France, Sweden, Ukraine, Czech, Hungary, and Slovakia, since December 2022. The lures used in the SmugX campaign betray the threat actor's target profile and indicates espionage as the likely objective of the campaign.

A Chinese nation-state group has been observed targeting Foreign Affairs ministries and embassies in Europe using HTML smuggling techniques to deliver the PlugX remote access trojan on compromised systems. "The campaign uses new delivery methods to deploy a new variant of PlugX, an implant commonly associated with a wide variety of Chinese threat actors," Check Point said.

European organizations experienced a greater volume and frequency of BEC attacks over the last year, as compared to organizations in the United States, according to Abnormal Security. This included an analysis of traditional BEC attacks like executive impersonation, vendor-focused invoice, and payment fraud, as well as credential phishing, malware, and extortion.

Pro-Kremlin groups Anonymous Sudan, Killnet and Clop have other motivations than just hacktivism as they widen their attack field beyond political targets. The June 19 attack against the European Investment Bank may have been a salvo aimed at thwarting financial pipelines supporting Ukraine's war effort, although the motives of the threat groups are still subject to speculation, experts say.

The growing adoption of cloud has elevated cloud security fear for IT teams, as they grapple with the challenges and concerns arising from the widespread use of complex cloud environments while diligently addressing them, according to SUSE. Cloud security fear is growing. Data stores as top cloud security concern: 31% of respondents named data stores hosted by cloud or third parties as their top cloud security concern.

The threat actor uses a custom implant to compromise a specific TP-Link router model and steal information from it, as well as provide backdoor access to the attackers. "Horse Shell" implant found in TP-Link router firmware.

Eurocontrol confirmed on Friday its website has been "Under attack" since April 19, and said "Pro-Russian hackers" had claimed responsibility for the disruption. "The attack is causing interruptions to the website and web availability," a spokesperson told The Register.
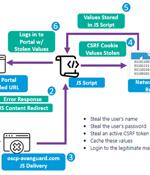
The advanced persistent threat actor known as Winter Vivern is now targeting officials in Europe and the U.S. as part of an ongoing cyber espionage campaign. "TA473 since at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to gain access to the email mailboxes of government entities in Europe," Proofpoint said in a new report.

Google has announced the startups chosen for its Cybersecurity Startups Growth Academy. The 15 selected startups are from eight countries and were chosen from over 120 applicants.
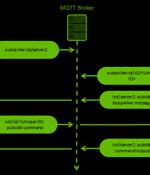
The China-aligned Mustang Panda actor has been observed using a hitherto unseen custom backdoor called MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023. "Unlike most of the group's malware, MQsTTang doesn't seem to be based on existing families or publicly available projects," ESET researcher Alexandre Côté Cyr said in a new report.