Security News

The Russia-linked APT29 threat actor has been attributed to an ongoing cyber espionage campaign targeting foreign ministries and diplomatic entities located in NATO member states, the European Union, and Africa. Nobelium's operations have been attributed to Russia's Foreign Intelligence Service, an organization that's tasked with protecting "Individuals, society, and the state from foreign threats."

A new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to gather strategic intelligence that aligns with Pyongyang's geopolitical interests since 2018. "APT43 is a prolific cyber operator that supports the interests of the North Korean regime," Mandiant researchers said in a detailed technical report published Tuesday.

A cyberespionage hacking group tracked as 'Bitter APT' was recently seen targeting the Chinese nuclear energy industry using phishing emails to infect devices with malware downloaders. Bitter is a suspected South Asian hacking group known to target high-profile organizations in the energy, engineering, and government sectors in the Asian-Pacific region.

As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple. Of the 55 zero-day bugs, 13 are estimated to have been abused by cyber espionage groups, with four others exploited by financially motivated threat actors for ransomware-related operations.

The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.
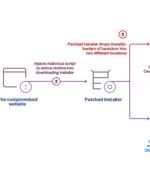
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. The differentiating factor in the latest attacks is a shift to social engineering to trick users into visiting compromised websites related to North Korea, according to a new report from Trend Micro released last week.

Groups tied to the Russian intelligence services will also continue to target geographic neighbors with disinformation campaigns, intelligence gathering, and possibly low-level disruptive attacks. Traditional espionage targets will continue to be a focus; for example, we saw evidence in August 2022 of Russian intelligence services using spear phishing emails to target staff at the Argonne and Brookhaven national laboratories in the US, which conduct cutting edge energy research.

An Iranian cyber espionage gang with ties to the Islamic Revolutionary Guard Corps has learned new methods and phishing techniques, and aimed them at a wider set of targets - including politicians, government officials, critical infrastructure and medical researchers - according to email security vendor Proofpoint. Over the past two years, the threat actor group that Proofpoint's researchers track as TA453 has branched out from its usual victims - academics, researchers, diplomats, dissidents, journalists and human rights workers - and adopted new means of attack.

A threat actor with a suspected China nexus has been linked to a set of espionage attacks in the Philippines that primarily relies on USB devices as an initial infection vector. The reliance on infected USB drives to propagate the malware is unusual if not new.

A threat actor with a suspected China nexus has been linked to a set of espionage attacks in the Philippines that primarily relies on USB devices as an initial infection vector. The reliance on infected USB drives to propagate the malware is unusual if not new.