Security News

Petro-Canada gas stations across Canada are impacted by technical problems preventing customers from paying with credit card or rewards points as its parent company, Suncor Energy, discloses they suffered a cyberattack.Suncor Energy is the 48th-largest public company in the world, and one of Canada's largest synthetic crude producers, having an annual revenue of $31 billion.

In this Help Net Security video, Jim Simpson, Director of Threat Intelligence at Searchlight Cyber, discusses how cybercriminals employ specialized strategies when targeting energy companies. This is primarily due to the sensitive and valuable information these organizations hold and their critical role in infrastructure, making them particularly attractive for economic and geopolitical disruption.

Malware designed to disrupt electric power grids was likely developed by a Russian contractor, according to Mandiant's threat intel team that discovered the malicious software and dubbed it CosmicEnergy. The team say it's likely a contractor created the malware as a red-teaming tool for simulated power disruption exercises hosted by Rostelecom-Solar, a Russian cybersecurity company.

An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022. Targeted entities consist of seaports, energy companies, transit systems, and a major U.S. utility and gas company.

A cyberespionage hacking group tracked as 'Bitter APT' was recently seen targeting the Chinese nuclear energy industry using phishing emails to infect devices with malware downloaders. Bitter is a suspected South Asian hacking group known to target high-profile organizations in the energy, engineering, and government sectors in the Asian-Pacific region.

Hitachi Energy confirmed it suffered a data breach after the Clop ransomware gang stole data using a zero-day GoAnyway zero-day vulnerability. Hitachi Energy is a department of Japanese engineering and technology giant Hitachi focused on energy solutions and power systems.
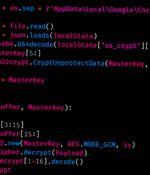
A previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part of a cyber espionage campaign that has been active since at least June 2022. Prominent countries targeted include Azerbaijan, Tajikistan, Kyrgyzstan, Turkmenistan, and other Commonwealth of Independent States nations.

A new threat actor named 'YoroTrooper' has been running cyber-espionage campaigns since at least June 2022, targeting government and energy organizations in Commonwealth of Independent States countries. Cisco Talos reports having evidence of YoroTrooper exfiltrating large volumes of data from infected endpoints, including account credentials, cookies, and browsing histories.

The Russia-affiliated Sandworm used yet another wiper malware strain dubbed NikoWiper as part of an attack that took place in October 2022 targeting an energy sector company in Ukraine. The use of SDelete is notable, as it suggests that Sandworm has been experimenting with the utility as a wiper in at least two different instances to cause irrevocable damage to the targeted organizations in Ukraine.

Colombian energy company Empresas Públicas de Medellín suffered a BlackCat/ALPHV ransomware attack on Monday, disrupting the company's operations and taking down online services. The Prosecutor's Office later confirmed to EL COLOMBIANO that ransomware was behind the attack on EPM that caused devices to be encrypted and data to be stolen.