Security News
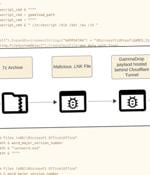
The threat actor known as Gamaredon has been observed leveraging Cloudflare Tunnels as a tactic to conceal its staging infrastructure hosting a malware called GammaDrop. The activity is part of an...

The integrity of our online ecosystem heavily relies on domain registries, which serve as the foundation for secure and trusted digital experiences. However, threats like Domain Name System (DNS)...

Hijacking domains using a ‘Sitting Ducks attack’ remains an underrecognized topic in the cybersecurity community. Few threat researchers are familiar with this attack vector, and knowledge is...

Read more about DNS hijacking and how organizations can prevent it.
Google on Wednesday announced a new partnership with the Global Anti-Scam Alliance (GASA) and DNS Research Federation (DNS RF) to combat online scams. The initiative, which has been codenamed the...

Infoblox’s Universal DDI solution could help stop cyber threat actors earlier.

Threat actors have hijacked more than 35,000 registered domains in so-called Sitting Ducks attacks that allow claiming a domain without having access to the owner's account at the DNS provider or...

The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that...

Decentralized finance crypto exchange dYdX announced on Tuesday that the website for its older v3 trading platform has been compromised. dYdX also warned users not to visit or interact with the hacked dydx[.

Security researchers are claiming a spate of DNS hijackings at web3 businesses is linked to Squarespace's acquisition of Google Domains last year. According to the researchers' report, Squarespace pre-registered a bunch of email addresses it thought would be useful to have set up as domain admins following the migration without checking if the email accounts existed.