Security News

After spending five years poring over port scan results, infosec firm Imperva reckons there's about 12,000 vulnerability-containing databases accessible through the internet. The news might prompt responsible database owners to double-check their updates and patching status, given the increasing attractiveness of databases and their contents to criminals and hostile foreign states alike.

This article can help you quantify the level of security of your databases on a scale of 1 to 10. Rating 2 is for databases where both the database and operating system are configured by following industry standards and best practices.

McDonald's UK Monopoly VIP game kicked off at the end of August, and a recent round of emails sent to winners of the game's various prizes included more than a coupon for free fries. The franchise accidentally inserted passwords for a McDonald's server that hosted information tied to the UK Monopoly VIP game.

McDonald's customers who won a prize draw competition got more than they hoped for after the burger chain emailed them login credentials for development and production databases used to power the campaign. The first person to report the blunder to McDonald's, startup founder Connor Greig, told The Register: "It's a bit weird," adding that code strings containing the credentials looked as if they had "Been formatted into the email by accident."

A bug in the McDonald's Monopoly VIP game in the United Kingdom caused the login names and passwords for the game's database to be sent to all winners. After skipping a year due to COVID-19, McDonald's UK launched their popular Monopoly VIP game on August 25th, where customers can enter codes found on purchase food items for a chance to win a prize.

Infosec outfit Wiz has revealed that Microsoft's flagship Azure database Cosmos DB could have been exploited to grant any Azure user full admin access - including the ability to read, write and delete data - to any Cosmos DB instance on Azure. Wiz has named the flaw ChaosDB. "By exploiting a chain of vulnerabilities in the Jupyter Notebook feature of Cosmos DB, a malicious actor can query information about the target Cosmos DB Jupyter Notebook," reads Wiz's explanation.
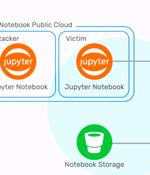
Cloud infrastructure security company Wiz on Thursday revealed details of a now-fixed Azure Cosmos database vulnerability that could have been potentially exploited to grant any Azure user full admin access to other customers' database instances without any authorization. Cosmos DB is Microsoft's proprietary NoSQL database that's advertised as "a fully managed service" that "Takes database administration off your hands with automatic management, updates and patching."
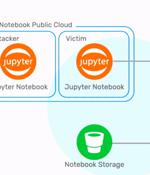
Cloud infrastructure security company Wiz on Thursday revealed details of a now-fixed Azure Cosmos database vulnerability that could have been potentially exploited to grant any Azure user full admin access to other customers' database instances without any authorization. Cosmos DB is Microsoft's proprietary NoSQL database that's advertised as "a fully managed service" that "Takes database administration off your hands with automatic management, updates and patching."

AT&T says that they did not suffer a data breach after a well-known threat actor claimed to be selling a database containing the personal information of 70 million customers. The hacker states that they are willing to sell it immediately for $1 million.

With insights into query performance and explain plans, as well as automatic correlation of query metrics with application and infrastructure metrics, Database Monitoring provides engineers and database administrators the visibility they need to quickly find and fix application performance issues that arise from slow running database queries. Datadog Database Monitoring builds on the existing ability to monitor the general health and availability of the database and underlying infrastructure by allowing users to pinpoint the exact queries that impact application performance and user experience.