Security News
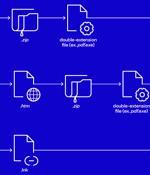
The threat actors behind RedLine and Vidar information stealers have been observed pivoting to ransomware through phishing campaigns that spread initial payloads signed with Extended Validation code signing certificates. In the incident investigated by the cybersecurity company, an unnamed victim is said to have first received a piece of info stealer malware with EV code signing certificates, followed by ransomware using the same delivery technique.
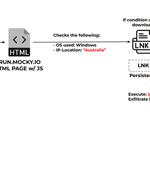
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium. "In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang's Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs," security researchers Niraj Shivtarkar and Avinash Kumar said.
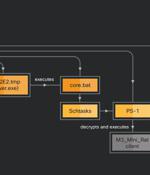
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021. "The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses Advanced Installer's Custom Actions feature to make the software installers execute the malicious scripts," Cisco Talos researcher Chetan Raghuprasad said in a technical report.

Cybercriminals create hundreds of thousands of counterfeit domains that mimic well-known brands for financial gain. These fake domains serve multiple malicious purposes, such as sending phishing emails, hosting fraudulent websites, rerouting web traffic, and distributing malware.

If you got snubbed by the object of your affections on dating app Coffee Meets Bagel in late August, don't feel bad, the company says its systems were down due to cyber baddies. Access to the service was finally restored on September 3 after the "Team spent days working around the clock to rebuild our system from online backups so that daters could securely get back online."

A cyberattack campaign is targeting exposed Microsoft SQL databases, aiming to deliver ransomware and Cobalt Strike payloads. The attackers target exposed MS SQL servers by brute-forcing access credentials.
"And with businesses now leveraging the reach of social media for advertising, attackers have a new, highly-lucrative type of attack to add to their arsenal - hijacking business accounts." Cyber attacks targeting Meta Business and Facebook accounts have gained popularity over the past year, courtesy of activity clusters such as Ducktail and NodeStealer that are known to raid businesses and individuals operating on Facebook.
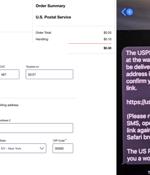
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct identity theft and financial fraud. "The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information and payment credentials from victims, in the furtherance of identity theft and credit card fraud," Resecurity said in an analysis published last week.

Adversary-sponsored research contests on cybercriminal forums focus on new methods of attack and evasion, according to Sophos. The contests mirror legitimate security conference 'Call For Papers' and provide the winners considerable financial rewards and recognition from peers and also potential jobs.
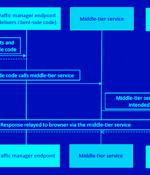
Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID application by taking advantage of an abandoned reply URL. "An attacker could leverage this abandoned URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for access tokens," Secureworks Counter Threat Unit said in a technical report published last week. Reply URL, also called redirect URI, refers to the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token.