Security News

One told to take down posts that said nice things about WP Engine Organisers of WordCamps, community-organized events for WordPress users, have been ordered to take down some social media posts...

Attackers have exploited an XSS vulnerability (CVE-2024-37383) in the Roundcube Webmail client to target a governmental organization of a CIS country, Positive Technologies (PT) analysts have...

Threat actors have been exploiting a vulnerability in the Roundcube Webmail client to target government organizations in the Commonwealth of Independent States (CIS) region, the successor of the...

Unknown threat actors have been observed attempting to exploit a now-patched security flaw in the open-source Roundcube webmail software as part of a phishing attack designed to steal user...

It's called leaving the door wide open – especially in Proxmox A critical bug in Kubernetes Image Builder could allow unauthorized SSH access to virtual machines (VMs) thanks to default...

Another blow for IT software house and its customers A critical, hardcoded login credential in SolarWinds' Web Help Desk line has been exploited in the wild by criminals, according to the US...

33.9% of tech professionals report a shortage of AI security skills, particularly around emerging vulnerabilities like prompt injection, according to O’Reilly. This highlights the need for...

Home and small business security company ADT disclosed it suffered a breach after threat actors gained access to its systems using stolen credentials and exfiltrated employee account data. [...]
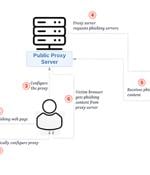
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past year, indicating that it's being used by a large number of...

In this Help Net Security interview, Omer Cohen, Chief Security Officer at Descope, discusses the impact of identity federation on organizational security and user experience. He explains how this...