Security News

A nascent and legitimate penetration testing framework known as Nighthawk is likely to gain threat actors' attention for its Cobalt Strike-like capabilities. There are no indications that a leaked or cracked version of Nighthawk is being weaponized by threat actors in the wild, Proofpoint researcher Alexander Rausch said in a write-up.

The Google Cloud Threat Intelligence team has open-sourced YARA Rules and a VirusTotal Collection of indicators of compromise to help defenders detect Cobalt Strike components in their networks. "We are releasing to the community a set of open-source YARA Rules and their integration as a VirusTotal Collection to help the community flag and identify Cobalt Strike's components and its respective versions," said Google Cloud Threat Intelligence security engineer Greg Sinclair.

Google Cloud's intelligence research and applications team has created and released a collection of 165 YARA rules to help defenders flag Cobalt Strike components deployed by attackers. Cobalt Strike, a legitimate adversary simulation tool used by pentesters and cyber red teams, has also become threat actors' preferred post-exploitation tool.

Google Cloud last week disclosed that it identified 34 different hacked release versions of the Cobalt Strike tool in the wild, the earliest of which shipped in November 2012. The versions, spanning 1.44 to 4.7, add up to a total of 275 unique JAR files, according to findings from the Google Cloud Threat Intelligence team.
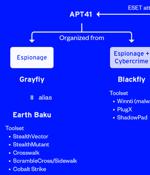
The victimology patterns and the targeted sectors overlap with attacks mounted by a distinct sister group of APT41 known as Earth Baku, the Japanese cybersecurity company added. Some of Earth Baku's malicious cyber activities have been tied to groups called by other cybersecurity firms ESET and Symantec under the names SparklingGoblin and Grayfly, respectively.

A previously unknown Chinese APT hacking group dubbed 'Earth Longzhi' targets organizations in East Asia, Southeast Asia, and Ukraine. The threat actors have been active since at least 2020, using custom versions of Cobalt Strike loaders to plant persistent backdoors on victims' systems.
HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems. Cobalt Strike is a commercial red-team framework that's mainly used for adversary simulation, but cracked versions of the software have been actively abused by ransomware operators and espionage-focused advanced persistent threat groups alike.

A new phishing campaign targets US and New Zealand job seekers with malicious documents installing Cobalt Strike beacons for remote access to victims' devices. The discovery comes from researchers at Cisco Talos who observed two different phishing lures, both targeting job seekers and leading to the deployment of Cobalt Strike.
A social engineering campaign leveraging job-themed lures is weaponizing a years-old remote code execution flaw in Microsoft Office to deploy Cobalt Strike beacons on compromised hosts. "The payload discovered is a leaked version of a Cobalt Strike beacon," Cisco Talos researchers Chetan Raghuprasad and Vanja Svajcer said in a new analysis published Wednesday.
Someone is flooding Cobalt Strike servers operated by former members of the Conti ransomware gang with anti-Russian messages to disrupt their activity. The operators of Conti ransomware completed turning off their internal infrastructure in May this year but its members have dispersed to other ransomware gangs.