Security News
A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in a new cyber espionage campaign designed to facilitate the delivery of the Cobalt Strike...

No malware crew linked to this latest red-teaming tool yet Attackers are using Splinter, a new post-exploitation tool, to wreak havoc in victims' IT environments after initial infiltration,...
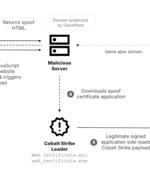
Chinese-speaking users are the target of a "highly organized and sophisticated attack" campaign that is likely leveraging phishing emails to infect Windows systems with Cobalt Strike payloads....

A Taiwanese government-affiliated research institute that specializes in computing and associated technologies was breached by nation-state threat actors with ties to China, according to new findings from Cisco Talos. The unnamed organization was targeted as early as mid-July 2023 to deliver a variety of backdoors and post-compromise tools like ShadowPad and Cobalt Strike.

Europol just announced that a week-long operation at the end of June dropped nearly 600 IP addresses that supported illegal copies of Cobalt Strike. "Used as a foothold, it has proven to be highly effective at providing a persistent backdoor to victims, facilitating intrusions of all forms. This disruption is to be welcomed, removing Cobalt Strike infrastructure used by criminals is always a good thing."

A coordinated law enforcement operation codenamed MORPHEUS has felled close to 600 servers that were used by cybercriminal groups and were part of an attack infrastructure associated with the...

Europol coordinated a joint law enforcement action known as Operation Morpheus, which led to the takedown of almost 600 Cobalt Strike servers used by cybercriminals to infiltrate victims' networks. "Older, unlicensed versions of the Cobalt Strike red teaming tool were targeted during a week of action coordinated from Europol's headquarters between 24 and 28 June," said Europol.
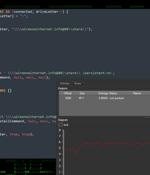
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also...
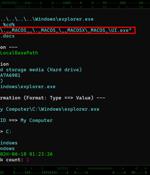
Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as Taiwan Semiconductor Manufacturing Company (TSMC) that are designed to deliver Cobalt...
Hackers engaging in cyber espionage have targeted Chinese-speaking semiconductor companies with TSMC-themed lures that infect them with Cobalt Strike beacons. The campaign spotted by EclecticIQ focuses on firms based in Taiwan, Hong Kong, and Singapore, with the observed TTPs bearing similarities to previous activities linked to Chinese state-backed threat groups.