Security News

In this Help Net Security interview, Alex Freedland, CEO at Mirantis, discusses the cloud security challenges that CISOs need to tackle as multi-cloud and hybrid environments become the norm. He...

The threat actors behind the AndroxGh0st malware are now exploiting a broader set of security flaws impacting various internet-facing applications, while also deploying the Mozi botnet malware....
High-profile entities in India have become the target of malicious campaigns orchestrated by the Pakistan-based Transparent Tribe threat actor and a previously unknown China-nexus cyber espionage...

Google has announced that, by the end of 2025, multi-factor authentication (MFA) – aka 2-step verification – will become mandatory for all Google Cloud accounts. “Given the sensitive nature of...

Google's cloud division has announced that it will enforce mandatory multi-factor authentication (MFA) for all users by the end of 2025 as part of its efforts to improve account security. "We will...

Google has announced that multi-factor authentication (MFA) will be mandatory on all Cloud accounts by the end of 2025 to enhance security. [...]

Discover how AI amplifies cloud security risks and how to mitigate them, with insights from Tenable’s Liat Hayun on managing data sensitivity, misconfigurations, and over-privileged access.

Emeraldwhale gang looked sharp – until it made a common S3 bucket mistake A criminal operation dubbed Emeraldwhale has been discovered after it dumped more than 15,000 credentials belonging to...

A global large-scale dubbed "EmeraldWhale" exploited misconfigured Git configuration files to steal over 15,000 cloud account credentials from thousands of private repositories. [...]
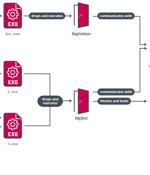
A government entity and a religious organization in Taiwan were the target of a China-linked threat actor known as Evasive Panda that infected them with a previously undocumented post-compromise...