Security News

Cybersecurity researchers have disclosed details of a now-patched zero-day flaw in Google Cloud Platform that could have enabled threat actors to conceal an unremovable, malicious application inside a victim's Google account. "The vulnerability allows attackers to gain permanent and unremovable access to a victim's Google account by converting an already authorized third-party application into a malicious trojan app, leaving the victim's personal data exposed forever," Astrix said in a report.

These predictions underscore the rapidly evolving landscape of Kubernetes and cloud security, emphasizing the need for organizations to stay informed and adopt comprehensive security solutions to protect their digital assets. In response, Uptycs, the first unified CNAPP and XDR platform, released a whitepaper, "14 Kubernetes and Cloud Security Predictions for 2023 and How Uptycs Meets Them Head-On" addressing the most pressing challenges and trends in Kubernetes and cloud security for 2023.
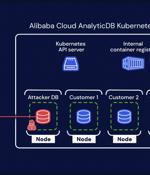
A chain of two critical flaws has been disclosed in Alibaba Cloud's ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access sensitive data belonging to other customers. "The vulnerabilities potentially allowed unauthorized access to Alibaba Cloud customers' PostgreSQL databases and the ability to perform a supply chain attack on both Alibaba database services, leading to an RCE on Alibaba database services," cloud security firm Wiz said in a new report shared with The Hacker News.

"The kernel failed to protect applications that attempted to protect against Spectre v2, leaving them open to attack from other processes running on the same physical core in another hyperthread," the vulnerability disclosure explains. Linux kernel 6.0 debuts, Linus Torvalds teases 'core new things' coming in version 6.1 Older AMD, Intel chips vulnerable to data-leaking 'Retbleed' Spectre variant Apple gets lawsuit over Meltdown and Spectre dismissed Boffins release tool to decrypt Intel microcode.

Open source software and software supply chain security risks continue to be a primary concern for developers and organizations. According to a 2022 study by electronic design and automation company Synopsys, 84% of open source software codebases contained at least one known vulnerability - a nearly 4% increase from last year - and 48% contained a high-risk vulnerability.

On Friday, five days into a massive outage impacting its cloud services, Western Digital finally provided customers with a workaround to access their files. The complete list of services that were down throughout this week includes My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS 5, SanDisk ibi, and SanDisk Ixpand Wireless Charger, together with linked mobile, desktop, and web apps.

Western Digital announced today that its network has been breached and an unauthorized party gained access to multiple company systems. "Upon discovery of the incident, the Company implemented incident response efforts and initiated an investigation with the assistance of leading outside security and forensic experts," Western Digital says in the disclosure.

The research showed that the majority of IT teams leverage more than one IT infrastructure, a trend that's expected to intensify in the future, but struggle with visibility of data across environments with only 40% reporting complete visibility into where their data resides. "Organizations are grappling with current application and data management across the edge, different clouds and in the core. There's a need in the market for a cloud operating model to help build, operate, use, and govern a hybrid multicloud to support all types of applications - starting today and planning for tomorrow," Caswell continued.

The AlienFox toolkit is being hawked on Telegram as a way to compromise misconfigured hosts on cloud services platforms and harvest sensitive information like API keys and other secrets, according to security shop SentinelOne. While the AlienFox scripts can be used against a range of web services, they primarily target cloud-based and software-as-a-service email hosting services, Delamotte wrote.

Multi-cloud data storage, once merely a byproduct of the great cloud migration, has now become a strategy for data management. As ransomware attacks continue to rise at a 13% growth rate year over year, surely more cloud storage simply equals more data vulnerability gaps to fill, right? New developments in data technology address these concerns.