Security News
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as...

Citrix has urged admins to "Immediately" apply a fix for CVE-2023-4966, a critical information disclosure bug that affects NetScaler ADC and NetScaler Gateway, admitting it has been exploited. Plus, there's a proof-of-concept exploit, dubbed Citrix Bleed, now on GitHub.

Citrix warned admins today to secure all NetScaler ADC and Gateway appliances immediately against ongoing attacks exploiting the CVE-2023-4966 vulnerability.NetScaler appliances must be configured as a Gateway or an AAA virtual server to be vulnerable to attacks.

A recently patched Citrix NetScaler ADC/Gateway information disclosure vulnerability has been exploited by attackers in the wild since late August 2023, Mandiant researchers have revealed.They exploited CVE-2023-4966 to hijack existing authenticated sessions, which means that they were able to effectively bypass multifactor authentication requirements.

Citrix is warning of exploitation of a recently disclosed critical security flaw in NetScaler ADC and Gateway appliances that could result in exposure of sensitive information. Tracked as...

A critical vulnerability tracked as CVE-2023-4966 in Citrix NetScaler ADC/Gateway devices has been actively exploited as a zero-day since late August, security researchers announced. A report from Mandiant disclosed that it found signs of CVE-2023-4966 being exploited in the wild since August for stealing authentication sessions and hijacking accounts.

Citrix NetScaler ADC and NetScaler Gateway are impacted by a critical severity flaw that allows the disclosure of sensitive information from vulnerable appliances. "Cloud Software Group strongly urges affected customers of NetScaler ADC and NetScaler Gateway to install the relevant updated versions of NetScaler ADC and NetScaler Gateway as soon as possible," reads Citrix's security bulletin.
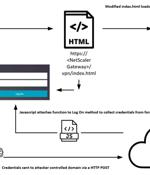
A recently disclosed critical flaw in Citrix NetScaler ADC and Gateway devices is being exploited by threat actors to conduct a credential harvesting campaign. IBM X-Force, which uncovered the...

Hackers are conducting a large-scale campaign to exploit the recent CVE-2023-3519 flaw in Citrix NetScaler Gateways to steal user credentials. The flaw is a critical unauthenticated remote code execution bug discovered as a zero-day in July that impacts Citrix NetScaler ADC and NetScaler Gateway.

A known threat actor specializing in ransomware attacks is believed to be behind a recent campaign that targeted unpatched internet-facing Citrix NetScaler systems to serve as an initial foothold into enterprise networks. "Our data indicates strong similarity between attacks using CVE-2023-3519 and previous attacks using a number of the same TTPs," Sophos researchers shared.