Security News

A federal grand jury has charged a former Broadcom engineer with stealing trade secrets and using them while working at a new employer - a Chinese chip start-up. Kim allegedly lifted the trade secrets from one of Broadcom's employee-only repositories as he prepared to leave the company in July of 2020.

US feds were spotted raiding a warehouse belonging to Chinese payment terminal manufacturer PAX Technology in Jacksonville, Florida, on Tuesday, with speculation abounding that the machines contained preinstalled malware. PAX Technology is headquartered in Shenzhen, China, and is one of the largest electronic payment providers in the world.

A joint announcement from the Ministry of Health and the National Cyber Directorate in Israel describes a spike in ransomware attacks over the weekend that targeted the systems of nine health institutes in the country. In the joint announcement, the Israeli government states that the attempts resulted in no damage to the hospitals and the medical organizations, thanks to national-level coordination and the quick and decisive response of the local IT teams.

A 36-year-old man from Portage, Michigan, was arrested on Thursday for allegedly renting thousands of textbooks from Amazon and selling them rather than returning them. Rew Birge, US Attorney for the Western District of Michigan, said Geoffrey Mark Hays Talsma has been indicted on charges of mail and wire fraud, transporting stolen property across state lines, aggravated identity theft, and lying to the FBI. Also indicted were three alleged co-conspirators: Gregory Mark Gleesing, 43, and Lovedeep Singh Dhanoa, 25, both from Portage, Michigan, and Paul Steven Larson, 32, from Kalamazoo, Michigan.

A Chinese-speaking hacking group exploited a zero-day vulnerability in the Windows Win32k kernel driver to deploy a previously unknown remote access trojan. The malware, known as MysterySnail, was found by Kaspersky security researchers on multiple Microsoft Servers between late August and early September 2021.

Blackberry's Research and Intelligence Team has uncovered three phishing schemes targeting Indian nationals, and says a Chinese state-sponsored malware gang is the culprit. Blackberry identified the responsible party as APT41 - a prolific Chinese state-sponsored cyberthreat group that has carried out what Fireye called "Espionage activity in parallel with financially motivated operations" since at least 2012.

Chinese cyber espionage group APT41 has been linked to seemingly disparate malware campaigns, according to fresh research that has mapped together additional parts of the group's network infrastructure to hit upon a state-sponsored campaign that takes advantage of COVID-themed phishing lures to target victims in India. APT41 is a moniker assigned to a prolific Chinese cyber threat group that carries out state-sponsored espionage activity in conjunction with financially motivated operations for personal gain as far back as 2012.
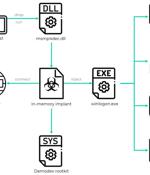
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems. Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a "Sophisticated multi-stage malware framework" that allows for providing persistence and remote control over the targeted hosts.

A previously undocumented backdoor that was recently found targeting an unnamed computer retail company based in the U.S. has been linked to a longstanding Chinese espionage operation dubbed Grayfly. The cybersecurity firm attributed the intrusion to a group it tracks as SparklingGoblin, an adversary believed to be connected to the Winnti malware family.

Microsoft has shared technical details about a now-fixed, actively exploited critical security vulnerability affecting SolarWinds Serv-U managed file transfer service that it has attributed with "High confidence" to a threat actor operating out of China. "The Serv-U SSH server is subject to a pre-auth remote code execution vulnerability that can be easily and reliably exploited in the default configuration," Microsoft Offensive Research and Security Engineering team said in a detailed write-up describing the exploit.