Security News
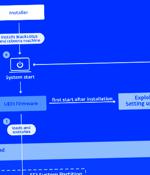
A stealthy Unified Extensible Firmware Interface bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.

Given these dynamics and the massive market opportunities for cybersecurity professionals, talent churn poses a significant threat to security teams. Gartner research shows that compliance-centric cybersecurity programs, low executive support, and subpar industry-level maturity are all indicators of an organization that does not view security risk management as critical to business success.

Brave Browser version 1.47 was released yesterday, adding the Snowflake extension in the software's settings, enabling users to turn their devices into proxies that help users in censored countries connect to Tor. Brave had already added support for Tor Bridges in Private Windows with Tor in version 1.44, released in September 2022, helping users bypass restrictions in the countries using the company's own resources.

Red Balloon Security disclosed multiple, critical architectural vulnerabilities in the Siemens SIMATIC and SIPLUS S7-1500 Series PLC that allow for bypass of all protected boot features. Exploitation of these vulnerabilities could allow offline attackers to generate arbitrary encrypted firmware that are bootable on all Siemens S7-1500 series PLC CPU modules.

A financially motivated threat actor tracked as Scattered Spider was observed attempting to deploy Intel Ethernet diagnostics drivers in a BYOVD attack to evade detection from EDR security products. The BYOVD technique involves threat actors using a kernel-mode driver known to be vulnerable to exploits as part of their attacks to gain higher privileges in Windows.

Cisco warned customers today of a critical authentication bypass vulnerability with public exploit code affecting multiple end-of-life VPN routers. The security flaw was found in the web-based management interface of Cisco Small Business RV016, RV042, RV042G, and RV082 routers by Hou Liuyang of Qihoo 360 Netlab.

Six malicious packages on PyPI, the Python Package Index, were found installing information-stealing and RAT malware while using Cloudflare Tunnel to bypass firewall restrictions for remote access. The malicious packages attempt to steal sensitive user information stored in browsers, run shell commands, and use keyloggers to steal typed secrets.

A South Africa-based threat actor known as Automated Libra has been observed employing CAPTCHA bypass techniques to create GitHub accounts in a programmatic fashion as part of a freejacking campaign dubbed PURPLEURCHIN. The group "Primarily targets cloud platforms offering limited-time trials of cloud resources in order to perform their crypto mining operations," Palo Alto Networks Unit 42 researchers William Gamazo and Nathaniel Quist said. PURPLEURCHIN first came to light in October 2022 when Sysdig disclosed that the adversary created as many as 30 GitHub accounts, 2,000 Heroku accounts, and 900 Buddy accounts to scale its operation.

Popular instant messaging service WhatsApp has launched support for proxy servers in the latest version of its Android and iOS apps, letting users circumvent government-imposed censorship and internet shutdowns. "Choosing a proxy enables you to connect to WhatsApp through servers set up by volunteers and organizations around the world dedicated to helping people communicate freely," the Meta-owned company said.

Starting today, WhatsApp allows users to connect via proxy servers due to Internet shutdowns or if their governments block the service in their country. The new proxy support option is available to all users running the latest WhatsApp iOS and Android applications.