Security News

Mandiant has identified a novel method to bypass contemporary browser isolation technology and achieve command-and-control C2 operations. [...]

In an effort to turn the tide, Mozilla is testing a fresh approach that could persuade more people to switch their default browser on Windows during the installation of the browser. [...]

Mozilla is testing a fresh approach that could persuade more people to switch their default browser on Windows. [...]

The rise of SaaS and cloud-based work environments has fundamentally altered the cyber risk landscape. With more than 90% of organizational network traffic flowing through browsers and web...
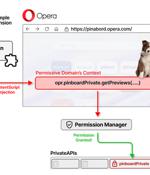
A now-patched security flaw in the Opera web browser could have enabled a malicious extension to gain unauthorized, full access to private APIs. The attack, codenamed CrossBarking, could have made...

Microsoft has disclosed details about a now-patched security flaw in Apple's Transparency, Consent, and Control (TCC) framework in macOS that has likely come under exploitation to get around a...

Mozilla has revealed that a critical security flaw impacting Firefox and Firefox Extended Support Release (ESR) has come under active exploitation in the wild. The vulnerability, tracked as...

A new 'FakeUpdate' campaign targeting users in France leverages compromised websites to show fake browser and application updates that spread a new version of the WarmCookie malware. [...]
The Browser Company has introduced an Arc Bug Bounty Program to encourage security researchers to report vulnerabilities to the project and receive rewards. [...]

Altered versions of legitimate Android apps associated with Spotify, WhatsApp, and Minecraft have been used to deliver a new version of a known malware loader called Necro. Kaspersky said some of...