Security News

Locks that use Bluetooth Low Energy to authenticate keys are vulnerable to remote unlocking. The research focused on Teslas, but the exploit is generalizable.

A novel Bluetooth relay attack can let cybercriminals more easily than ever remotely unlock and operate cars, break open residential smart locks, and breach secure areas. "An attacker can falsely indicate the proximity of Bluetooth LE devices to one another through the use of a relay attack," U.K.-based cybersecurity company NCC Group said.

Vulnerabilities found in Bluetooth Low Energy gives hackers access to numerous devices. A critical flaw found in Bluetooth Low Energy receivers may grant cyber criminals entry to anything from personal devices, such as phones or laptops, to even cars and houses.

Tesla Model 3 and Y owners, beware: the passive entry feature on your vehicle could potentially be fooled by a new form of relay attack. Discovered and tested by researchers at NCC Group, the attack allows anyone with a tool similar to NCC's to relay the Bluetooth Low Energy signal from a smartphone that has been paired with a Tesla back to the vehicle.

Security researchers at the NCC Group have developed a tool to carry out a Bluetooth Low Energy relay attack that bypasses all existing protections to authenticate on target devices. BLE technology is used in a wide spectrum of products, from electronics like laptops, mobile phones, smart locks, and building access control systems to cars like Tesla Model 3 and Model Y. Pushing out fixes for this security problem is complicated, and even if the response is immediate and coordinated, it would still take a long time for the updates to trickle to impacted products.

Microsoft has fixed a known Bluetooth issue causing some Windows 10 systems to crash with a blue screen of death after installing the January KB5009596 cumulative update. The list of affected Windows versions includes only client platforms: Windows 10 21H2, Windows 10 21H1, and Windows 10 20H2. "After installing KB5009596 or later updates, some organizations which have Windows devices paired to Bluetooth devices might receive an error message 'Your device ran into a problem and needs to restart.' with a blue screen and 'Stop code: IRQ NOT LESS OR EQUAL'," Microsoft explains.

A Bluetooth phone designed to evoke the carefree days of early childhood has been found to instead threaten the very adult prospect of being surveilled in your home. The phone is the Fisher Price Chatter Special Edition, a device that adds Bluetooth and a speaker to the smiling, brightly coloured, wheeled, rotary dial phone on which it's previously been possible to make calls only by using one's imagination.

Security vendor F-Secure has faked a COVID test result on a Bluetooth-equipped home COVID Test. The firm tested the Ellume COVID-19 Home Test, a device selected specifically because it uses a "Bluetooth connected analyzer for use with an app on your phone."
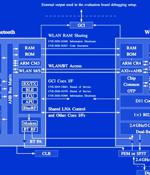
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "Combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless communications, such as Wi-Fi, Bluetooth, and LTE. "We provide empirical evidence that coexistence, i.e., the coordination of cross-technology wireless transmissions, is an unexplored attack surface," a group of researchers from the Technical University of Darmstadt's Secure Mobile Networking Lab and the University of Brescia said in a new paper.

The vice president of the US, Kamala Harris, was mocked by commentators this week for her aversion to Bluetooth on security grounds. Security professionals think she has a point - given her position.