Security News
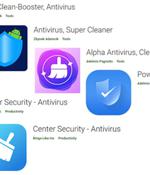
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot. "SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News.

Threat actors have been distributing malicious applications under the guise of seemingly harmless shopping apps to target customers of eight Malaysian banks since at least November 2021. "The threat actors use these fake e-shop applications to phish for banking credentials," ESET said.

Threat analysts following the activity of LightBasin, a financially motivated group of hackers, report the discovery of a previously unknown Unix rootkit that is used to steal ATM banking data and conduct fraudulent transactions. In a new report by Mandiant, researchers present further evidence of LightBasin activity, focusing on bank card fraud and the compromise of crucial systems.

Escobar mobile malware targets 190 banking and financial apps, steals 2FA codes. Mobile malware is becoming increasingly powerful against banking and financial applications, especially on Android operating systems.

Consumers are digitally connected in almost all facets of their lives - and it's evident they expect the same from their banks and payment experiences, with consumers overwhelmingly expressing a preference for digital offerings from their financial institutions. "This study highlights how more than ever, consumer banking is about digital interactions first, and that they must create that digital experience with security at its foundation," said Jenn Markey, VP of product marketing at Entrust.
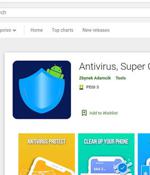
The threat actor behind a nascent Android banking trojan named SharkBot has managed to evade Google Play Store security barriers by masquerading as an antivirus app. Where SharkBot stands apart is in its ability to carry out the unauthorized transactions via Automatic Transfer Systems, which stands in contrast to TeaBot, which requires a live operator to interact with the infected devices to conduct the malicious activities.
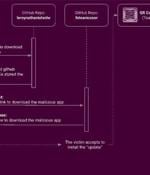
An Android banking trojan designed to steal credentials and SMS messages has been observed sneaking past Google Play Store protections to target users of more than 400 banking and financial apps from Russia, China, and the U.S. "TeaBot RAT capabilities are achieved via the device screen's live streaming plus the abuse of Accessibility Services for remote interaction and key-logging," Cleafy researchers said in a report. Also known by the name Anatsa, TeaBot first emerged in May 2021, camouflaging its malicious functions by posing as seemingly innocuous PDF document and QR code scanner apps that are distributed via the official Google Play Store instead of third-party apps stores or via fraudulent websites.

New Xenomorph Android malware targets more than 50 banking and financial applications. Figure B. The Alien malware has more overall capabilities than Xenomorph, which is far more targeted at stealing banking information.

The overall number of attacks on mobile users is down, but they're getting slicker, both in terms of malware functionality and vectors, researchers say. The company's mobile products and technologies detected 97,661 new mobile banking trojans, along with 3,464,756 malicious installation packages and 17,372 new mobile ransomware trojans.
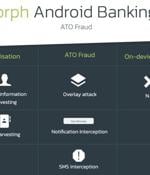
A new Android banking trojan with over 50,000 installations has been observed distributed via the official Google Play Store with the goal of targeting 56 European banks and carrying out harvesting sensitive information from compromised devices. Xenomorph, like Alien and ERMAC, is yet another example of an Android banking trojan that's focused on circumventing Google Play Store's security protections by masquerading as productivity apps such as "Fast Cleaner" to trick unaware victims into installing the malware.