Security News
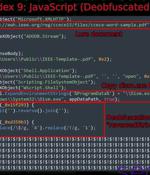
A new phishing campaign has been observed employing tax-themed lures to deliver a stealthy backdoor payload as part of attacks targeting Pakistan. Cybersecurity company Securonix, which is...

The Chinese Winnti hacking group is using a new PHP backdoor named 'Glutton' in attacks on organizations in China and the U.S., and also in attacks on other cybercriminals. [...]

Thai government officials have emerged as the target of a new campaign that leverages a technique called DLL side-loading to deliver a previously undocumented backdoor dubbed Yokai. "The target of...

The Russian nation-state actor tracked as Secret Blizzard has been observed leveraging malware associated with other threat actors to deploy a known backdoor called Kazuar on target devices...

The threat actors behind the More_eggs malware have been linked to two new malware families, indicating an expansion of its malware-as-a-service (MaaS) operation. This includes a novel...

A previously undocumented threat activity cluster dubbed Earth Minotaur is leveraging the MOONSHINE exploit kit and an unreported Android-cum-Windows backdoor called DarkNimbus to facilitate...
The China-linked threat actor known as MirrorFace has been attributed to a new spear-phishing campaign mainly targeting individuals and organizations in Japan since June 2024. The aim of the...
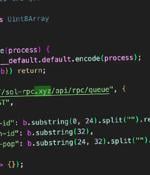
Cybersecurity researchers are alerting to a software supply chain attack targeting the popular @solana/web3.js npm library that involved pushing two malicious versions capable of harvesting users'...

Threat actors are using public exploits for a critical authentication bypass flaw in ProjectSend to upload webshells and gain remote access to servers. [...]

Russia-aligned APT group RomCom was behind attacks that leveraged CVE-2024-9680, a remote code execution flaw in Firefox, and CVE-2024-49039, an elevation of privilege vulnerability in Windows...