Security News

Blighty’s latest stab at encryption? A secret order to pry open iCloud, sources claim The UK's Home Office refuses to either confirm or deny reports that it recently ordered Apple to create a...

A Chinese hacking group is hijacking the SSH daemon on network appliances by injecting malware into the process for persistent access and covert operations. [...]

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Food and Drug Administration (FDA) have issued alerts about the presence of hidden functionality in Contec CMS8000 patient...

Contec CMS8000, a patient monitor manufactured by a Chinese company, and Epsimed MN-120, which is the same monitor but relabeled, exfiltrate patients’ data to a hard-coded IP address and have a...

The US Cybersecurity and Infrastructure Security Agency (CISA) is warning that Contec CMS8000 devices, a widely used healthcare patient monitoring device, include a backdoor that quietly sends...

Stealing crypto is so 2024. Supply-chain attacks leading to data exfil pays off better? North Korea's Lazarus Group compromised hundreds of victims across the globe in a massive secret-stealing...
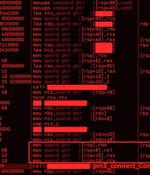
A financially motivated threat actor has been linked to an ongoing phishing email campaign that has been ongoing since at least July 2024 specifically targeting users in Poland and Germany. The...

A financially motivated threat actor has been targeting German and Polish-speaking users with info-stealing malware and TorNet, a previously undocumented .NET backdoor that leverages the Tor...

A newly discovered VPN backdoor uses some interesting tactics to avoid detection: When threat actors use backdoor malware to gain access to a network, they want to make sure all their hard work...

Who could be so interested in chips, manufacturing, and more, in the US, UK, Europe, Russia... Someone has been quietly backdooring selected Juniper routers around the world in key sectors...