Security News

A RansomHub affiliate is leveraging a new multi-function backdoor dubbed Betruger to perform various actions during their attacks, Symantec researchers have discovered. The Betruger backdoor The...
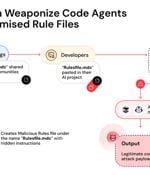
Cybersecurity researchers have disclosed details of a new supply chain attack vector dubbed Rules File Backdoor that affects artificial intelligence (AI)-powered code editors like GitHub Copilot...

Juniper Networks has released emergency security updates to patch a Junos OS vulnerability exploited by Chinese hackers to backdoor routers for stealthy access. [...]

The China-nexus cyber espionage group tracked as UNC3886 has been observed targeting end-of-life MX routers from Juniper Networks as part of a campaign designed to deploy custom backdoors,...

Chinese hackers are deploying custom backdoors on Juniper Networks Junos OS MX routers that have reached end-of-life (EoL) and no longer receive security updates. [...]

PLUS: Malaysia teams with Arm for local chip designs; NTT warns of possible breach; Samsung strikers settle; and more Asia in Brief India’s government has proposed giving its tax authorities...

The ubiquitous ESP32 microchip made by Chinese manufacturer Espressif and used by over 1 billion units as of 2023 contains an undocumented backdoor that could be leveraged for attacks. [...]

Over 1,000 websites powered by WordPress have been infected with a third-party JavaScript code that injects four separate backdoors. "Creating four backdoors facilitates the attackers having...

A first-of-its-kind legal challenge set to be heard this month, per reports Apple has reportedly filed a legal complaint with the UK's Investigatory Powers Tribunal (IPT) contesting the UK...

The threat actor known as Lotus Panda has been observed targeting government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with updated...