Security News
Hackers tied to the North Korean government have been observed using an updated version of a backdoor known as Dtrack targeting a wide range of industries in Germany, Brazil, India, Italy, Mexico, Switzerland, Saudi Arabia, Turkey and the U.S. "Dtrack allows criminals to upload, download, start or delete files on the victim host," Kaspersky researchers Konstantin Zykov and Jornt van der Wiel said in a report. Discovered in September 2019, the malware has been previously deployed in a cyber attack aimed at a nuclear power plant in India, with more recent intrusions using Dtrack as part of Maui ransomware attacks.
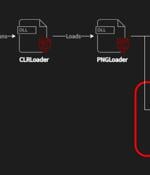
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.
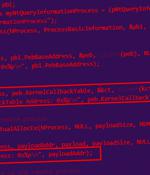
SideWinder, a prolific nation-state actor mainly known for targeting Pakistan military entities, compromised the official website of the National Electric Power Regulatory Authority to deliver a tailored malware called WarHawk. "The newly discovered WarHawk backdoor contains various malicious modules that deliver Cobalt Strike, incorporating new TTPs such as KernelCallBackTable injection and Pakistan Standard Time zone check in order to ensure a victorious campaign," Zscaler ThreatLabz said.

As one of the oldest banking trojans - dating back to the mid-2000s - the software nasty has a number of variants and been given a few monikers, including URSNIF, Gozi, and ISFB. It's crossed paths with other malware families, had its source code leaked twice since 2016 and, according to Mandiant, is now less a single malware family than a "Set of related siblings." In a report this week, Mandiant researchers Sandor Nemes, Sulian Lebegue, and Jessa Valdez wrote that a strain of URSNIF's RM3 version is no longer a banking trojan but a generic backdoor, similar to the short-lived Saigon variant.

A previously undocumented, fully undetectable PowerShell backdoor is being actively used by a threat actor who has targeted at least 69 entities. When first detected, the PowerShell backdoor was not seen as malicious by any vendors on the VirusTotal scanning service.

Details have emerged about a previously undocumented and fully undetectable PowerShell backdoor that gains its stealth by disguising itself as part of a Windows update process. "The covert self-developed tool and the associated C2 commands seem to be the work of a sophisticated, unknown threat actor who has targeted approximately 100 victims," Tomer Bar, director of security research at SafeBreach, said in a new report.

SafeBreach Labs says it has detected a novel fully undetectable PowerShell backdoor, which calls into question the accuracy of threat naming. "The attack starts with a malicious Word document, which includes a macro that launches an unknown PowerShell script," said Bar.

A threat actor tracked as Polonium has been linked to over a dozen highly targeted attacks aimed at Israelian entities with seven different custom backdoors since at least September 2021. ESET's latest discovery of five more previously undocumented backdoors brings into focus an active espionage-oriented threat actor that's constantly refining and retooling its malware arsenal.

Abstract: Early backdoor attacks against machine learning set off an arms race in attack and defence development. Defences have since appeared demonstrating some ability to detect backdoors in models or even remove them.

Internet snoops have been caught concealing spyware in an old Windows logo in an attack on governments in the Middle East. The Witchetty gang used steganography to stash backdoor Windows malware - dubbed Backdoor.