Security News
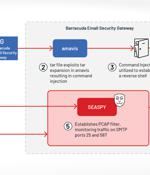
The U.S. Cybersecurity and Infrastructure Security Agency on Friday disclosed details of a "Novel persistent backdoor" called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway appliances. The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868, which allows for remote command injection.

The Russian nation-state actor known as BlueBravo has been observed targeting diplomatic entities throughout Eastern Europe with the goal of delivering a new backdoor called GraphicalProton, exemplifying the continuous evolution of the threat. The phishing campaign is characterized by the use of legitimate internet services for command-and-control obfuscation, Recorded Future said in a new report published Thursday.

Seems that there is a deliberate backdoor in the twenty-year-old TErrestrial Trunked RAdio standard used by police forces around the world. TETRA has been used in products, including radios, sold by Motorola, Airbus, and more.

The defense sector in Ukraine and Eastern Europe has been targeted by a novel. NET-based backdoor called DeliveryCheck that's capable of delivering next-stage payloads.
The financially motivated threat actor known as FIN8 has been observed using a "Revamped" version of a backdoor called Sardonic to deliver the BlackCat ransomware. Known to be active since at least 2016, the adversary was originally attributed to attacks targeting point-of-sale systems using malware such as PUNCHTRACK and BADHATCH. The group resurfaced after more than a year in March 2021 with an updated version of BADHATCH, following it up with a completely new bespoke implant called Sardonic, which was disclosed by Bitdefender in August 2021.
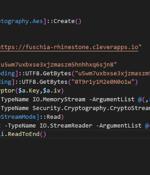
Charming Kitten, the nation-state actor affiliated with Iran's Islamic Revolutionary Guard Corps, has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured PowerShell backdoor called POWERSTAR. "There have been improved operational security measures placed in the malware to make it more difficult to analyze and collect intelligence," Volexity researchers Ankur Saini and Charlie Gardner said in a report published this week. Recent intrusions orchestrated by Charming Kitten have made use of other implants such as PowerLess and BellaCiao, suggesting that the group is utilizing an array of espionage tools at its disposal to realize its strategic objectives.

An unknown cryptocurrency exchange located in Japan was the target of a new attack earlier this month to deploy an Apple macOS backdoor called JokerSpy. Elastic Security Labs, which is monitoring the intrusion set under the name REF9134, said the attack led to the installation of Swiftbelt, a Swift-based enumeration tool inspired by an open-source utility called SeatBelt.

Foreign affairs ministries in the Americas have been targeted by a Chinese state-sponsored actor named Flea as part of a recent campaign that spanned from late 2022 to early 2023. The cyber attacks, per Broadcom's Symantec, involved a new backdoor codenamed Graphican.

The threat actor known as ChamelGang has been observed using a previously undocumented implant to backdoor Linux systems, marking a new expansion of the threat actor's capabilities. The malware, dubbed ChamelDoH by Stairwell, is a C++-based tool for communicating via DNS-over-HTTPS tunneling.

Symantec's threat research team, part of Broadcom, reports today that the threat actors have recently begun using USB malware to propagate to additional systems inside infected networks. Symantec's analysts report that Gamaredon's 2023 activity spiked between February and March 2023, while the hackers continued to maintain a presence on some compromised machines until May 2023.