Security News

Resecurity's AI-powered solutions provide proactive alerts and visibility of digital risks targeting the enterprise ecosystem. By joining the Microsoft Azure marketplace, Resecurity's software solutions will be easily accessible to the millions of Azure customers needing comprehensive cybersecurity management and monitoring.

Microsoft has expanded its confidential computing offering and now allows Azure cloud computing service customers to create hardware isolated virtual machines with Ephemeral OS disks. With this new public preview feature, Azure customers can create ephemeral OS disks only on the local VM storage, thus ensuring that data remains 100% confidential since it will never be sent to remote Azure Storage.

Azure Active Directory now allows admins to issue time-limited passcodes that can be used to register new passwordless authentication methods, during Windows onboarding, or to recover accounts easier when losing credentials or FIDO2 keys. Described by Microsoft as a Temporary Access Pass, they can be utilized to register authentication details after enabling TAP in the Azure AD authentication method policy via the Azure portal.
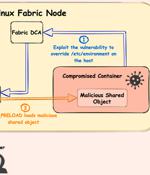
Cybersecurity researchers from Palo Alto Networks Unit 42 disclosed details of a new security flaw affecting Microsoft's Service Fabric that could be exploited to obtain elevated permissions and seize control of all nodes in a cluster. Azure Service Fabric is Microsoft's platform-as-a-service and a container orchestrator solution used to build and deploy microservices-based cloud applications across a cluster of machines.

Microsoft has fixed a container escape bug dubbed FabricScape in the Service Fabric application hosting platform that let threat actors escalate privileges to root, gain control of the host node, and compromise the entire SF Linux cluster. Additional details on how CVE-2022-30137 can be exploited to execute code and take over SF Linux clusters are available in Unit 42's report.

Microsoft has fixed a container escape vulnerability in the Service Fabric application hosting platform that would allow threat actors to escalate privileges to root, gain control of the host node, and compromise the entire SF Linux cluster. Additional details on how CVE-2022-30137 can be exploited to execute code and take over SF Linux clusters are available in Unit 42's report.

Resecurity, Inc. has identified a spike in phishing content delivered via Azure Front Door, a cloud CDN service provided by Microsoft. According to experts, such tactics confirm how the bad actors are continuously looking to enhance their tactics and procedures to avoid phishing detection using world-known cloud services.
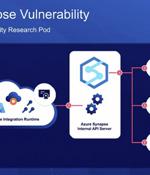
Microsoft has incorporated additional improvements to address the recently disclosed SynLapse security vulnerability in order to meet comprehensive tenant isolation requirements in Azure Data Factory and Azure Synapse Pipelines. The high-severity issue, tracked as CVE-2022-29972 and disclosed early last month, could have allowed an attacker to perform remote command execution and gain access to another Azure client's cloud environment.

Two security vendors - Orca Security and Tenable - have accused Microsoft of unnecessarily putting customers' data and cloud environments at risk by taking far too long to fix critical vulnerabilities in Azure. In a blog published today, Orca Security researcher Tzah Pahima claimed it took Microsoft several months to fully resolve a security flaw in Azure's Synapse Analytics that he discovered in January.

Microsoft sets multi-factor authentication as default for all Azure AD customers. In a new blog post, the company revealed that it's adding multi-factor authentication as the default security setting for existing Azure customers who haven't changed that setting on their own.