Security News

Haifei Li discovered that threat actors have been distributing Windows Internet Shortcut Files to spoof legitimate-looking files, such as PDFs, but that download and launch HTA files to install password-stealing malware. An Internet Shortcut File is simply a text file that contains various configuration settings, such as what icon to show, what link to open when double-clicked, and other information.
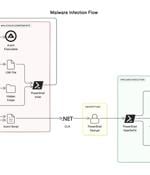
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations," Trellix security researchers Mathanraj Thangaraju and Sijo Jacob said.

Patch Tuesday Clear your Microsoft system administrator's diary: The bundle of fixes in Redmond's July Patch Tuesday is a doozy, with at least two bugs under active exploitation. The first of two vulnerabilities for sure under active exploit - CVE-2024-38080 - is a Windows Hyper-V elevation of privilege flaw with a 7.8-out-of-10 CVSS rating, which Microsoft deemed "Important."

Blast-RADIUS, an authentication bypass in the widely used RADIUS/UDP protocol, enables threat actors to breach networks and devices in man-in-the-middle MD5 collision attacks. [...]

A joint advisory from international cybersecurity agencies and law enforcement warns of the tactics used by the Chinese state-sponsored APT 40 hacking group and their hijacking of SOHO routers to launch cyberespionage attacks. Previously, APT40 was linked to a wave of attacks targeting over 250,000 Microsoft Exchange servers using the ProxyLogon vulnerabilities and campaigns involving exploiting flaws in widely used software, such as WinRAR. APT40 activity overview.

Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle attacks and bypass integrity checks under certain circumstances. "The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks," InkBridge Networks CEO Alan DeKok, who is the creator of the FreeRADIUS Project, said in a statement.

A new critical security vulnerability in the RADIUS protocol, dubbed BlastRADIUS, leaves most networking equipment open to Man-in-the-Middle attacks. To protect businesses from BlastRADIUS, "Every network switch, router, firewall, VPN concentrator, access point, and DSL gateway worldwide needs to be updated to add integrity and authentication checks for these packets," explains Alan DeKok, CEO of InkBridge Networks and one of the foremost experts on RADIUS servers.
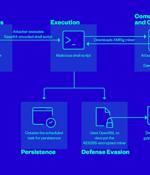
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.

Law enforcement agencies from eight nations, led by Australia, have issued an advisory that details the tradecraft used by China-aligned threat actor APT40 - aka Kryptonite Panda, GINGHAM TYPHOON, Leviathan and Bronze Mohawk - and found it prioritizes developing exploits for newly found vulnerabilities and can target them within hours. The advisory describes APT40 as a "State-sponsored cyber group" and the People's Republic of China as that sponsor.

ProPublica has a long investigative article on how the Cyber Safety Review Board failed to investigate the SolarWinds attack, and specifically Microsoft’s culpability, even though they were...