Security News

Security analysts have discovered and linked MoonBounce, "The most advanced" UEFI firmware implant found in the wild so far, to the Chinese-speaking APT41 hacker group. Kaspersky couldn't retrieve that payload for analysis or figure out how exactly the actors infected the UEFI firmware in the first place.

Attackers looking to exploit recently discovered Log4j vulnerabilities are also trying to take advantage of a previously undisclosed vulnerability in the SolarWinds Serv-U software. It affects version 15.2.5 and previous versions of Serv-U, and has been patched by SolarWinds in version 15.3.

Software supply chain attacks grew by more than 300% in 2021 compared to 2020, according to a study by Argon Security. According to the study, researchers discovered attackers focused most heavily on open source vulnerabilities and poisoning, code integrity issues, and exploiting the software supply chain process and supplier trust to distribute malware or backdoors.

SolarWinds has patched a Serv-U vulnerability discovered by Microsoft that threat actors actively used to propagate Log4j attacks to internal devices on a network. Microsoft says they discovered the vulnerability during their monitoring of the Log4j attacks.

RR Donnelly has confirmed that threat actors stole data in a December cyberattack, confirmed by BleepingComputer to be a Conti ransomware attack. While RRD initially said they were not aware of any client data stolen during the attack, on January 15th, the Conti ransomware gang claimed responsibility and began leaking 2.5GB of data allegedly stolen from RRD. However, a source told BleepingComputer that Conti soon removed the data from public view after RRD began further negotiations to prevent the release of data.
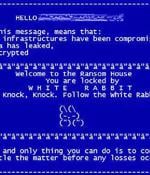
The financially motivated FIN8 actor, in all likelihood, has resurfaced with a never-before-seen ransomware strain called "White Rabbit" that was recently deployed against a local bank in the U.S. in December 2021. "One of the most notable aspects of White Rabbit's attack is how its payload binary requires a specific command-line password to decrypt its internal configuration and proceed with its ransomware routine," the researchers noted.

Clearly, the stakes are high - gaining access to a Box account could give cyberattackers access to a vast array of sensitive documents and data for both individuals and organizations. When a user goes to log on with his or her credentials, Box generates the cookies and the user is asked to navigate to an SMS verification page, where the person is instructed to enter a one-time passcode sent to an enrolled mobile phone.

A phishing campaign seen by email security provider Inky tries to trick its victims by inviting them to submit bids for alleged government projects. A phishing email that appears to come from an official government entity is especially deceptive as it carries an air of authority.

The mobile app that all attendees and athletes of the upcoming Beijing Winter Olympics must use to manage communications and documentation at the event has a "Devastating" flaw in the way it encrypts data that can allow for man-in-the-middle attacks that access sensitive user information, researchers have found. MY2022 is an app mandated for use by all attendees - including members of the press and athletes - of the 2022 Olympic Games in Beijing.

A new phishing campaign impersonating the United States Department of Labor asks recipients to submit bids to steal Office 365 credentials. The phishing campaign has been ongoing for at least a couple of months and utilizes over ten different phishing sites impersonating the government agency.