Security News

An advanced persistent threat group, with ties to Iran, is believed behind a phishing campaign targeting high-profile government and military Israeli personnel, according to a report by Check Point Software. Targets of the campaign included a senior leadership in the Israeli defense industry, the former U.S. Ambassador to Israel and the former Deputy Prime Minister of Israel.

Security researchers are warning that threat actors could hijack Office 365 accounts to encrypt for a ransom the files stored in SharePoint and OneDrive services that companies use for cloud-based collaboration, document management and storage. A ransomware attack targeting files on these services could have severe consequences if backups aren't available, rendering important data inaccessible to owners and working groups.

In this Help Net Security video, Chris Lehman, CEO at SafeGuard Cyber, talks about how adversaries are moving beyond email to attack companies through a wide range of digital communications platforms, including mobile messaging, collaboration, conferencing, CRM and social media. These social engineering attacks are difficult to detect and bypass standard security controls.

A newly discovered security vulnerability in modern Intel and AMD processors could let remote attackers steal encryption keys via a power side channel attack. This can have significant security implications on cryptographic libraries even when implemented correctly as constant-time code to prevent timing-based side channels, effectively enabling an attacker to leverage the execution time variations to extract sensitive information such as cryptographic keys.

A Malaysia-linked hacktivist group has attacked targets in India, seemingly in reprisal for a representative of the ruling Bharatiya Janata Party making remarks felt to be insulting to the prophet Muhammad. The BJP has ties to the Hindu Nationalist movement that promotes the idea India should be an exclusively Hindu nation. According to Indian threat intelligence vendor CloudSEK and US-based security and application delivery vendor Radware, Sharma's remarks caught the attention of a Malaysia-linked group called DragonForce that has launched attacks against Indian targets and sought assistance from others to do likewise under the banner "#OpsPatuk".

Microsoft claims to have finally fixed the Follina zero-day flaw in Windows as part of its June Patch Tuesday batch, which included security updates to address 55 vulnerabilities. Criminals and snoops can abuse the remote code execution bug, tracked as CVE-2022-30190, by crafting a file, such as a Word document, so that when opened it calls out to the Microsoft Windows Support Diagnostic Tool, which is then exploited to run malicious code, such spyware and ransomware.
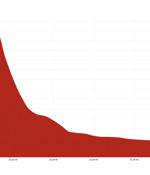
Cloudflare on Tuesday disclosed that it had acted to prevent a record-setting 26 million request per second distributed denial-of-service attack last week, making it the largest HTTPS DDoS attack detected to date. The web performance and security company said the attack was directed against an unnamed customer website using its Free plan and emanated from a "Powerful" botnet of 5,067 devices, with each node generating approximately 5,200 RPS at peak.

A new side-channel attack known as Hertzbleed allows remote attackers to steal full cryptographic keys by observing variations in CPU frequency enabled by dynamic voltage and frequency scaling. "In the worst case, these attacks can allow an attacker to extract cryptographic keys from remote servers that were previously believed to be secure. [.] Hertzbleed is a real, and practical, threat to the security of cryptographic software," the security researchers explain.

A new side-channel attack known as Hertzbleed allows remote attackers to steal full cryptographic keys by observing variations in CPU frequency enabled by dynamic voltage and frequency scaling. "In the worst case, these attacks can allow an attacker to extract cryptographic keys from remote servers that were previously believed to be secure. [.] Hertzbleed is a real, and practical, threat to the security of cryptographic software," the security researchers explain.

Internet infrastructure firm Cloudflare said today that it mitigated a 26 million request per second distributed denial-of-service attack, the largest HTTPS DDoS attack detected to date. The threat actor behind it likely used hijacked servers and virtual machines seeing that the attack originated from Cloud Service Providers instead of weaker Internet of Things devices from compromised Residential Internet Service Providers.