Security News

A microcosm of this upward trend involved exploits targeting public information sites and tied to political events, including the war in Ukraine and the midterm elections in the U.S. In response to the rise in politically motivated DDoS attacks, Google is offering a free service called Project Shield to government sites, news and independent journalists, sites related to elections and voting, and sites that cover human rights. The company reported a 400% rise in DDoS attacks on its customers during last year's election season in the U.S. In the second half of 2022, Project Shield saw over 25,000 such attacks against customers, many of them 100,000 queries per second in size.

American university researchers have developed a novel attack called "Near-Ultrasound Inaudible Trojan" that can launch silent attacks against devices powered by voice assistants, like smartphones, smart speakers, and other IoTs. The main principle that makes NUIT effective and dangerous is that microphones in smart devices can respond to near-ultrasound waves that the human ear cannot, thus performing the attack with minimal risk of exposure while still using conventional speaker technology.
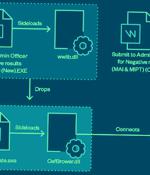
Attack chains mounted by the group commence with a spear-phishing email to deploy a wide range of tools for backdoor access, command-and-control, and data exfiltration. These messages come bearing with malicious lure archives distributed via Dropbox or Google Drive links that employ DLL side-loading, LNK shortcut files, and fake file extensions as arrival vectors to obtain a foothold and drop backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang.

TechCrunch has learned of dozens of organizations that used the affected GoAnywhere file transfer software at the time of the ransomware attack, suggesting more victims are likely to come forward. While the number of victims of the mass-hack is widening, the known impact is murky at best.
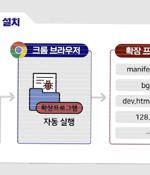
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The intrusions are designed to strike "Experts on the Korean Peninsula and North Korea issues" through spear-phishing campaigns, the agencies noted.

Public proof-of-concept exploits have landed for bugs in Netgear Orbi routers - including one critical command execution vulnerability. The four vulnerabilities are found in Netgear's Orbi mesh wireless system, including its main router and the satellite routers that extend WiFi networks.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products.With your permission we and our partners may use precise geolocation data and identification through device scanning.

Coinbase wallet and other decentralized crypto apps were found to be vulnerable to "Red pill attacks," a method that can be used to hide malicious smart contract behavior from security features. Security researchers at ZenGo Wallet have discovered that dapps, including the Coinbase Wallet, were vulnerable to a new attack that allows smart contracts to hide malicious behavior during transaction simulations.

A new malware botnet was discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit devices into DDoS swarm with the potential for massive attacks. Akamai's analysts created a C2 of their own and interacted with simulated infections to stage HinataBot for DDoS attacks to observe the malware in action and infer its attack capabilities.

The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.