Security News

The UK law enforcement office SEROCU, short for South East Regional Organised Crime Unit, this week reported the peculiar tale of one Ashley Liles, the literal Man in the Middle whom we referred to in the headline. These days, we usually expand the jargon term MitM to mean Manipulator in the Middle, not merely to avoid the gendered term "Man", but also because many, if not most, MitM attacks these days are performed by machines.

A suspected Iranian state-supported threat actor known as 'Agrius' is now deploying a new ransomware strain named 'Moneybird' against Israeli organizations. Check Point's researchers who discovered the new ransomware strain believe that Agrius developed it to help expand their operations, while the use of 'Moneybird' is yet another one of the threat group's attempts to cover their tracks.

A former IT security analyst at Oxford Biomedica has admitted, five years after the fact, to turning to the dark side - by hijacking a cyber attack against his own company in an attempt to divert any ransom payments to himself. Ashley Liles, of Letchworth Garden City, Hertfordshire, pleaded guilty at Reading Crown Court to blackmail and unauthorized access to a computer with intent to commit other offences on May 17 following an investigation by the South East Regional Organised Crime Unit.

The Computer Emergency Response Team of Ukraine has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign. In the attack chain described by the agency, the emails targeted an unspecified ministry and purported to be from the Embassy of Tajikistan in Ukraine.

Dish Network has admitted that a February cybersecurity incident and associated multi-day outage led to the extraction of data on nearly 300,000 people, while also appearing to indirectly admit it may have paid cybercriminals to delete said data. Dish customers can rest easy, at the very least, as the company said in a sample letter posted to the Maine Attorney General's breach notification website that customer databases weren't accessed and the stolen data belonged instead to employees both past and present, their family members, "And a limited number of other individuals" that Dish didn't specify.

German automotive and arms manufacturer Rheinmetall AG confirms that it suffered a BlackBasta ransomware attack that impacted its civilian business. On Saturday, May 20th, 2023, BlackBasta posted Rheinmetall on its extortion site along with samples of the data the hackers claimed to have stolen from the German company.
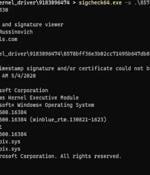
An unknown threat actor has been observed leveraging a malicious Windows kernel driver in attacks likely targeting the Middle East since at least May 2020. A key security measure to mitigate against malicious drivers is Driver Signature Enforcement, which ensures that only drivers signed by Microsoft can be loaded on the system.

The threat actor uses a custom implant to compromise a specific TP-Link router model and steal information from it, as well as provide backdoor access to the attackers. "Horse Shell" implant found in TP-Link router firmware.

The ALPHV ransomware group was observed employing signed malicious Windows kernel drivers to evade detection by security software during attacks. The POORTRY malware is a Windows kernel driver signed using stolen keys belonging to legitimate accounts in Microsoft's Windows Hardware Developer Program.

Today, the U.S. Cybersecurity & Infrastructure Security Agency ordered federal agencies to address three recently patched zero-day flaws affecting iPhones, Macs, and iPads known to be exploited in attacks. iPhone 6s, iPhone 7, iPhone SE, iPad Air 2, iPad mini, iPod touch, and iPhone 8 and later.